New Malware Technique Exploits Windows UI Automation
/ 1 min read
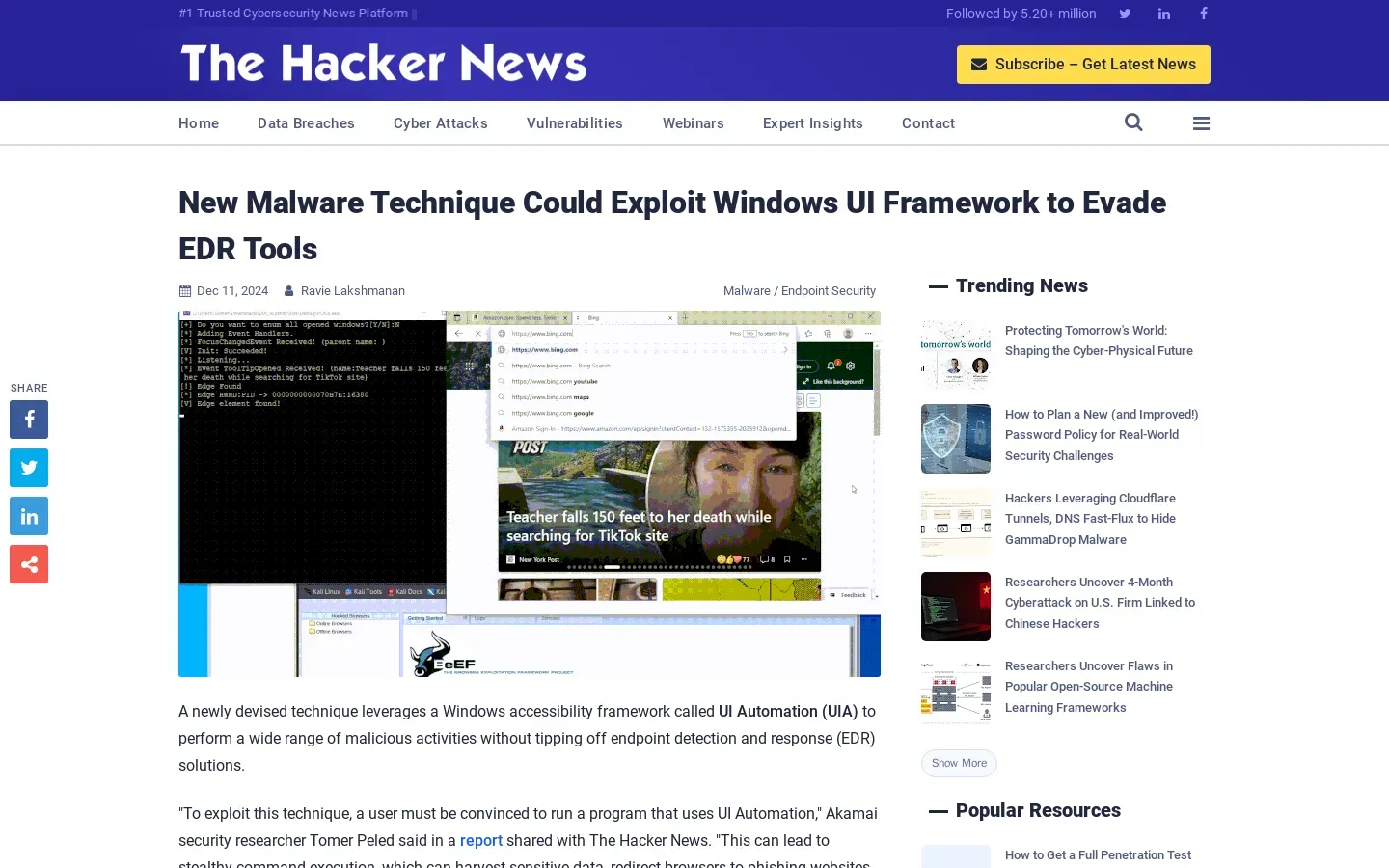
🦠 New malware technique exploits Windows UI Automation for stealthy attacks. A recent report by Akamai security researcher Tomer Peled reveals a method that leverages the Windows UI Automation (UIA) framework to conduct various malicious activities without detection by endpoint security systems. This technique requires users to run a program utilizing UIA, enabling attackers to execute commands, harvest sensitive data, and manipulate messaging applications like Slack and WhatsApp. The research highlights that UIA’s design, intended for assistive technologies, can be weaponized, allowing unauthorized access to UI elements and data. Additionally, a related vulnerability in the Distributed COM (DCOM) protocol could enable remote attacks, although these leave detectable indicators of compromise. The findings underscore the need for enhanced security measures against such exploitation methods.