Honeypot Analysis Enhanced by PCAP Data Collection
/ 1 min read
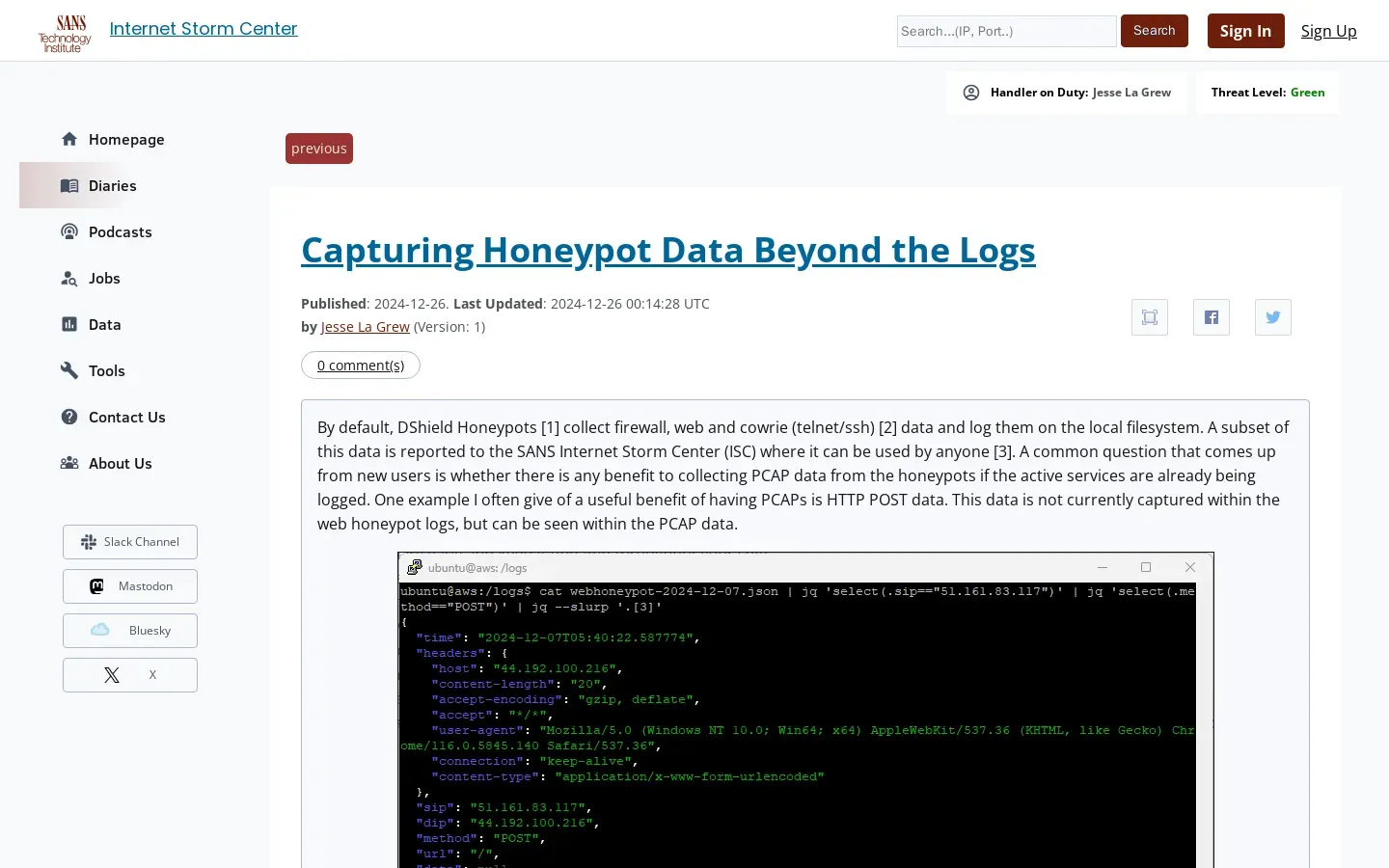
📦 The Importance of PCAP Data in Honeypot Analysis. DShield Honeypots primarily log firewall, web, and cowrie data, but the collection of PCAP data can provide significant insights, particularly for HTTP POST requests that are not captured in standard logs. By utilizing a Python script to extract and analyze UDP data from PCAP files, researchers can uncover valuable information about attempted communications, including unexpected traffic patterns on common ports like MySQL (port 3306). This analysis reveals that many data packets contain XML and SOAP envelopes, highlighting the potential for deeper insights into network activity. For those operating honeypots, incorporating PCAP data collection is recommended to enhance threat analysis capabilities.