LDAP Logging in Active Directory for Threat Detection
/ 1 min read
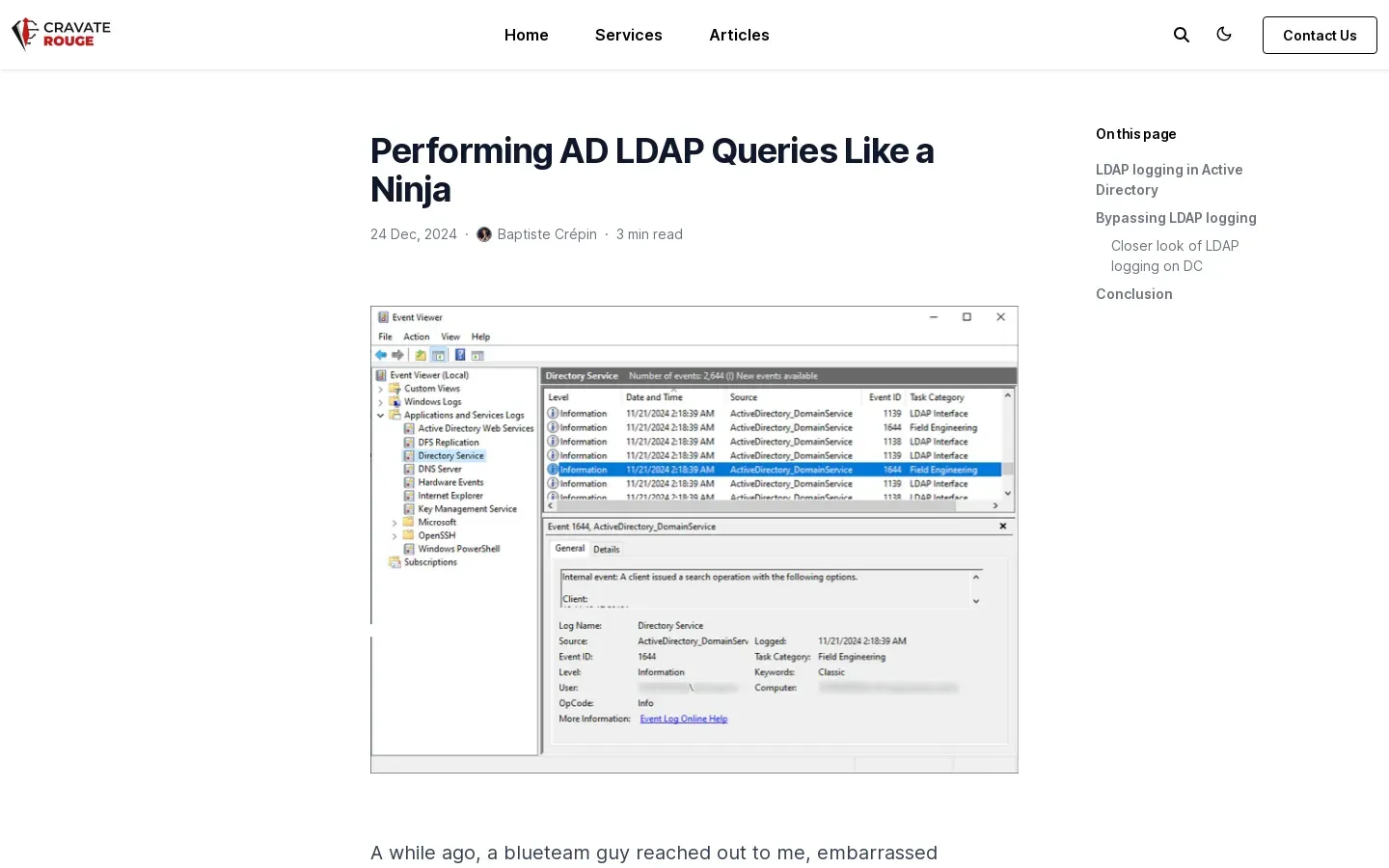
🔍 Understanding LDAP Logging in Active Directory for Threat Detection. The article explores the complexities of logging LDAP queries in Active Directory (AD) and the challenges faced by security teams in detecting potential threats. It outlines three common logging methods: client-side logging, network sniffing, and DC-side logging, noting that each has its vulnerabilities. The author emphasizes that DC-side logging requires specific registry configurations to capture all LDAP queries effectively, as default settings may overlook critical threats. Recommendations for red team members include using tools that support LDAP encryption and narrowing query scopes to avoid detection. The piece concludes that proper LDAP logging setup is essential for effective threat detection in AD environments.