Nuclei Vulnerability Allows Bypass of Signature Verification
/ 1 min read
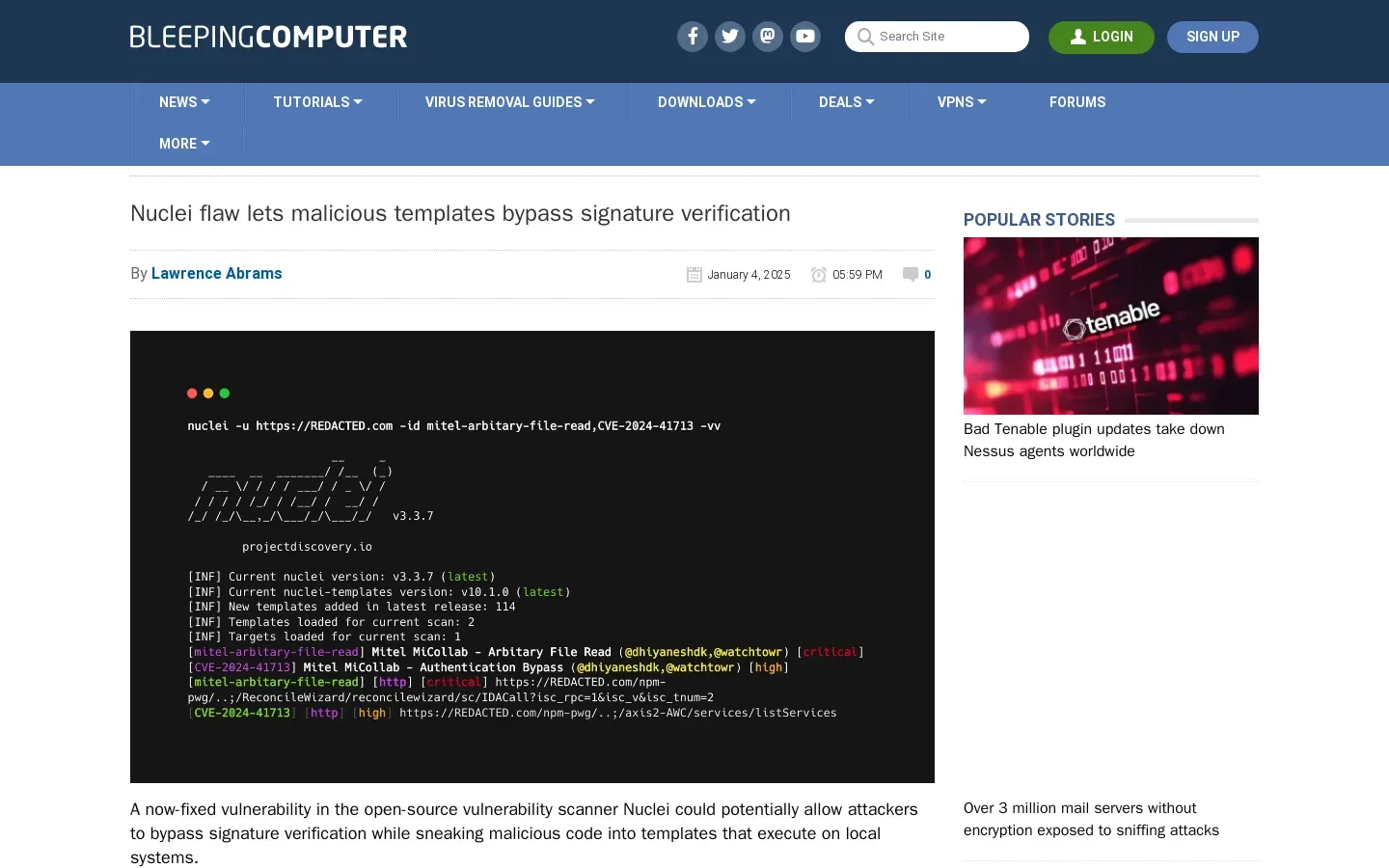
🧩 Nuclei vulnerability allows malicious templates to bypass signature verification. A recently discovered flaw in the open-source vulnerability scanner Nuclei, tracked as CVE-2024-43405, enables attackers to inject malicious code into templates that can execute on local systems. This vulnerability arises from discrepancies in how Go’s regex-based signature verification and the YAML parser handle line breaks, allowing modified templates to evade detection. Researchers at Wiz disclosed the issue to ProjectDiscovery, which has since released a fix in Nuclei v3.3.2. Users of older versions are urged to update immediately and consider running Nuclei in isolated environments to mitigate potential risks from malicious templates.
Source
Original