ESXi Ransomware Attacks Utilize SSH Tunneling Techniques
/ 1 min read
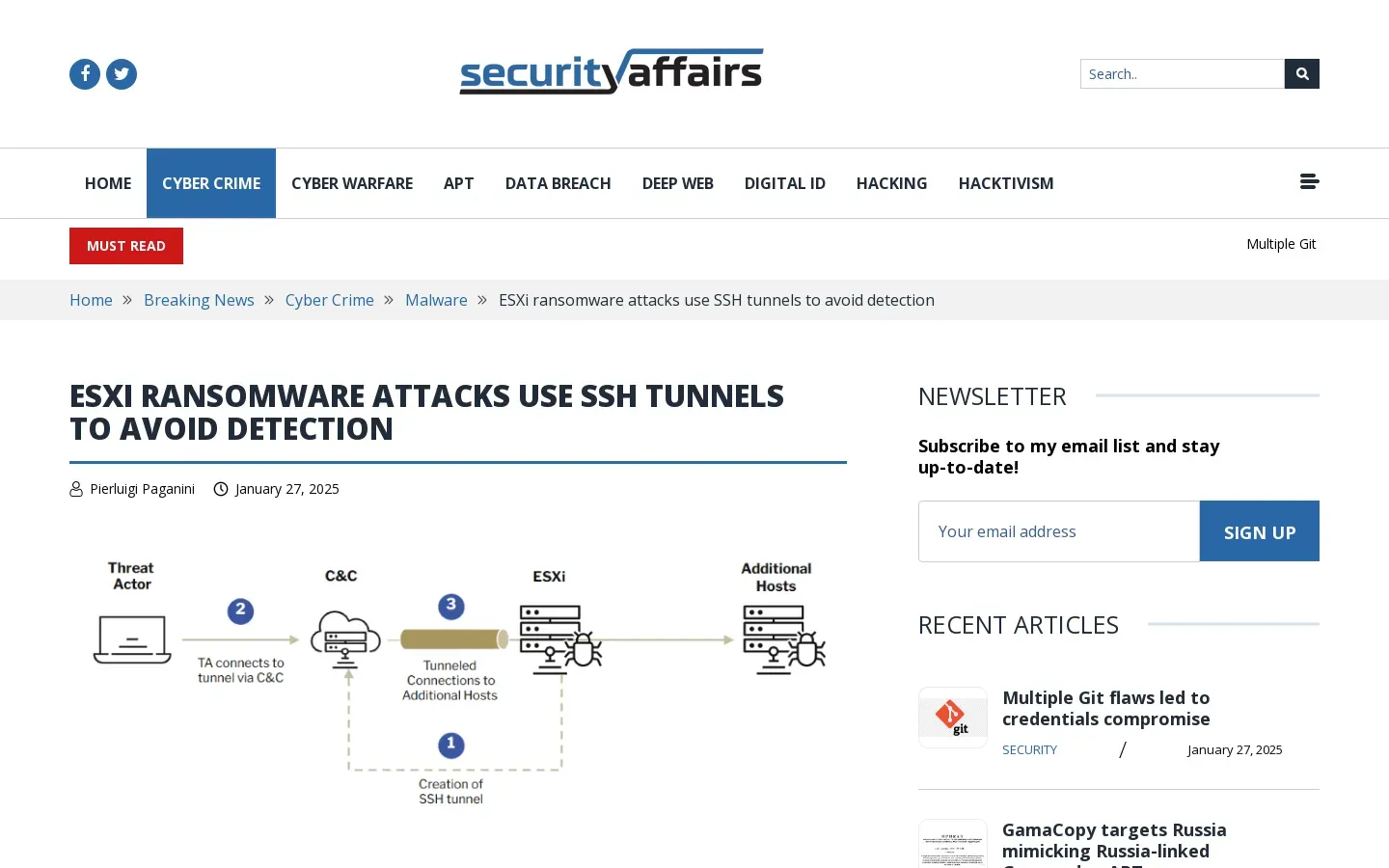
🔌 ESXi ransomware attacks leverage SSH tunneling for stealthy infiltration. Cybersecurity researchers at Sygnia have identified that threat actors are targeting virtualized environments through ESXi appliances, utilizing SSH tunneling to evade detection. By exploiting unmonitored ESXi systems, attackers gain access via administrative credentials or known vulnerabilities, establishing undetected communication channels with command and control servers. The resilience of ESXi appliances allows for persistent backdoors, complicating forensic investigations due to fragmented log files. To enhance monitoring, the report emphasizes the importance of configuring syslog forwarding to centralize event capture and improve detection of malicious activities associated with SSH tunneling techniques. Key log files are highlighted as critical for identifying potential attacks.