Double Fetch Vulnerabilities in Windows Kernel Explored
/ 1 min read
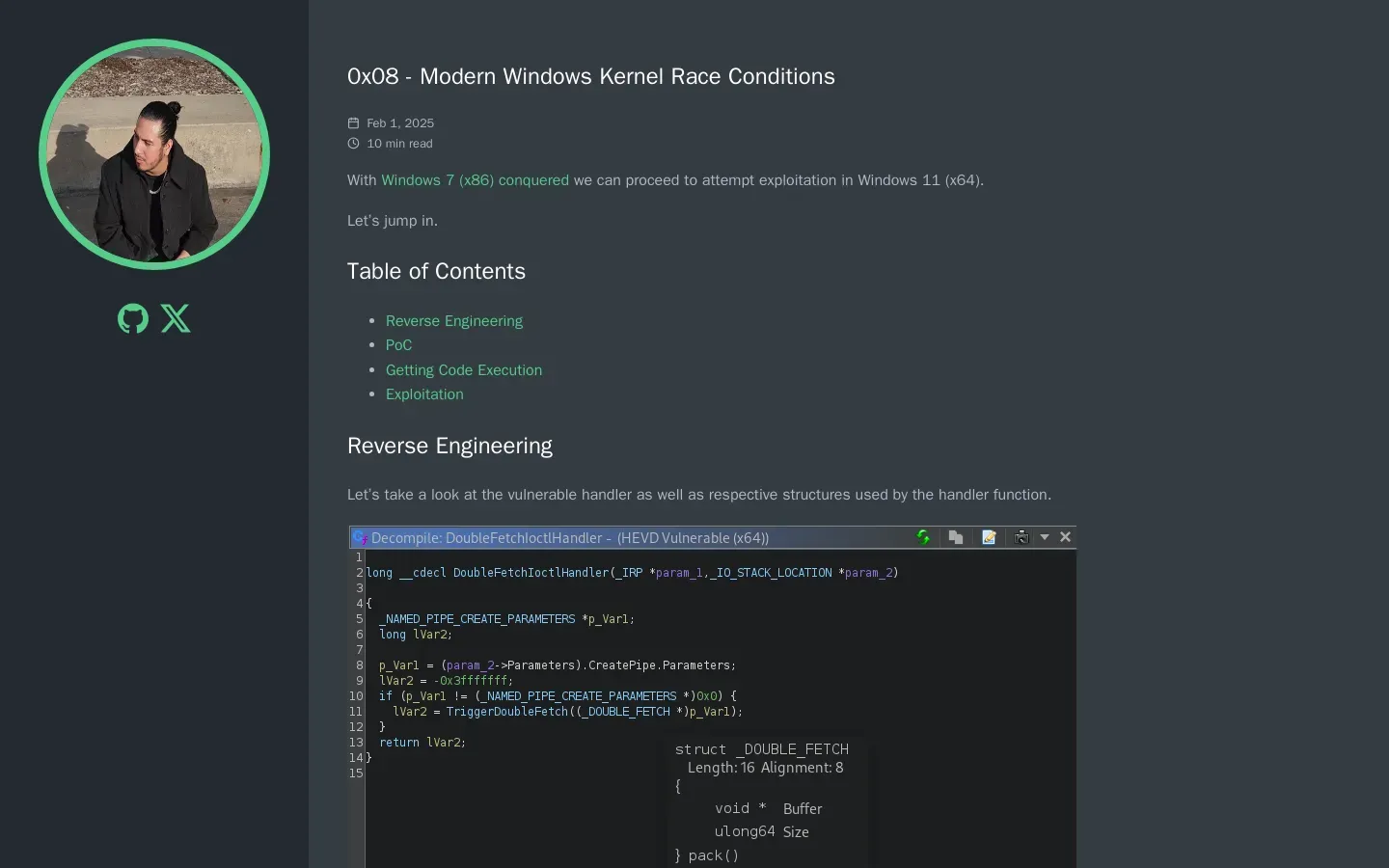
🪲 Exploring Double Fetch Vulnerabilities in Modern Windows Kernel. The article delves into the mechanics of Double Fetch vulnerabilities, highlighting how controlled input can be referenced multiple times, leading to potential race conditions. It outlines the process of crafting a proof of concept (PoC) to exploit this vulnerability, demonstrating how to overwrite a return address and gain control over the instruction pointer. The author discusses the challenges faced in finding suitable gadgets for a return-oriented programming (ROP) chain due to buffer contamination, ultimately suggesting a strategy to write the ROP chain beyond the return address overwrite. This exploration sheds light on the complexities of exploiting vulnerabilities within the Windows kernel environment.