iRISC Research Analyzes SHA256 Implementation Insights
/ 1 min read
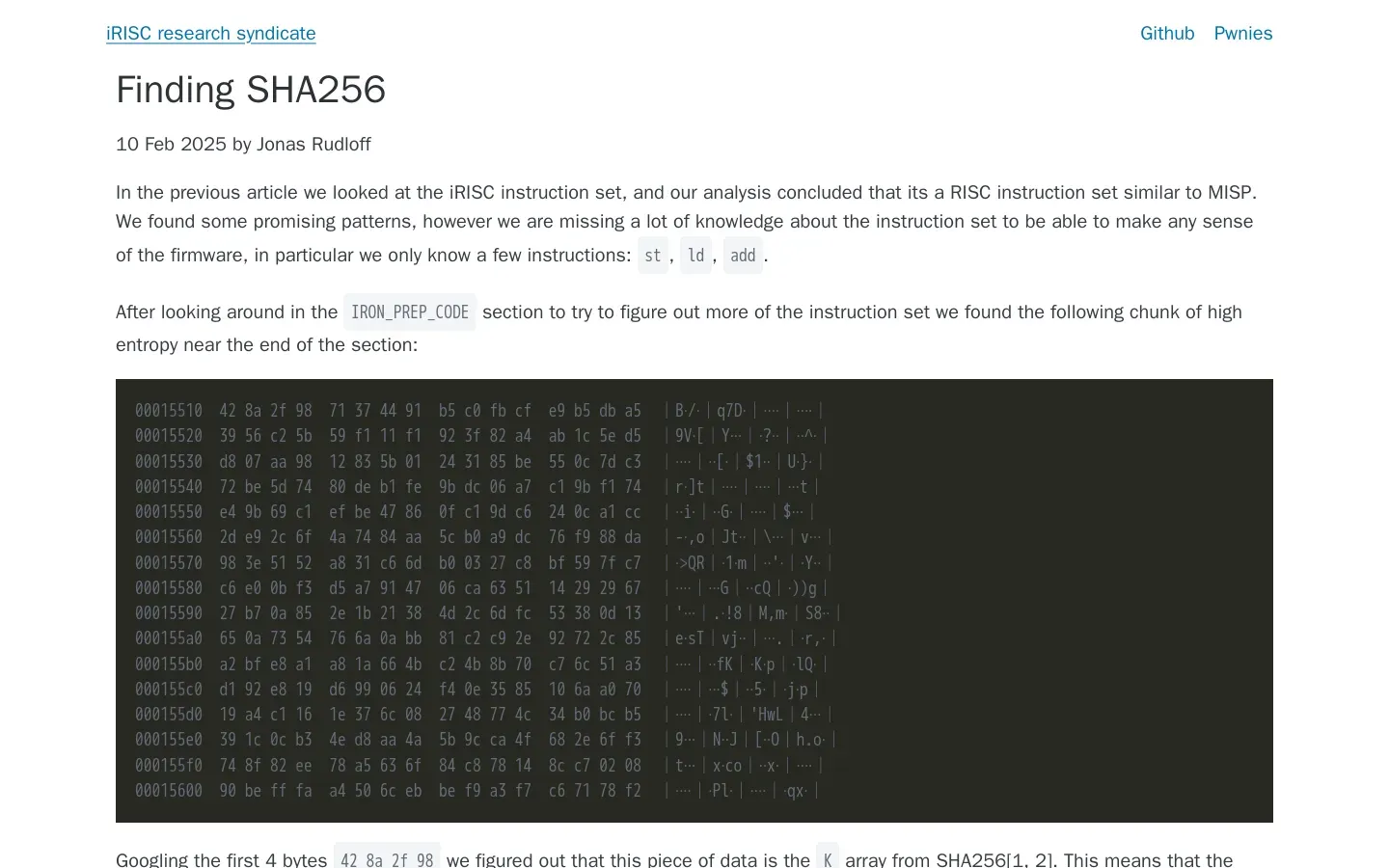
🔍 iRISC Research Uncovers SHA256 Implementation Insights. The iRISC research syndicate has made significant progress in understanding the iRISC instruction set, particularly through the analysis of its firmware, which likely includes an implementation of the SHA256 algorithm. By identifying high-entropy data and known constants from open-source SHA256 implementations, researchers have deduced the functionality of several instructions, including loading initialization constants and performing arithmetic operations. Their findings suggest a clearer understanding of ALU operations, branches, and calls within the instruction set, paving the way for further exploration of the iRISC architecture. The research highlights the potential for deeper analysis of the instruction set as more information becomes available.