AsyncRAT Malware Uses Null-AMSI to Evade Detection
/ 1 min read
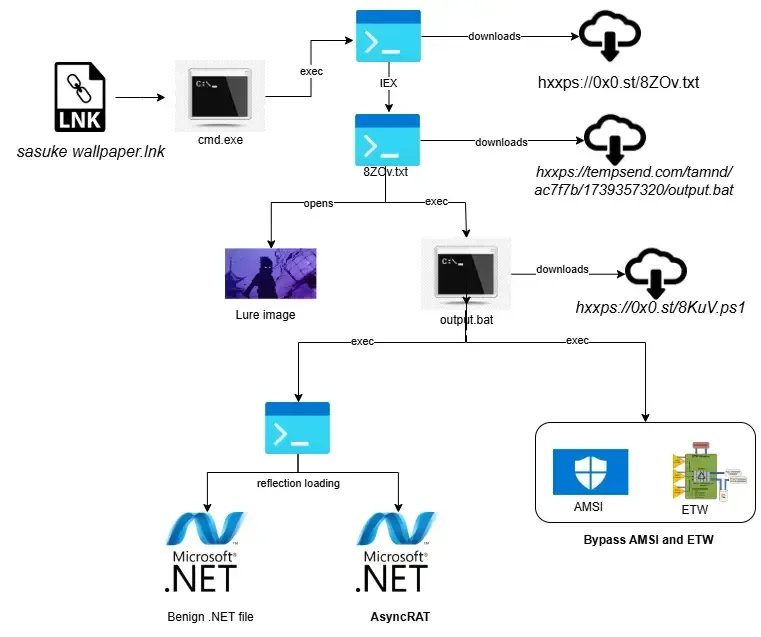
🎭 New malware campaign utilizes Null-AMSI to evade Windows security and deploy AsyncRAT. Cyble Research and Intelligence Labs (CRIL) has uncovered a sophisticated malware campaign that employs Null-AMSI to bypass Windows security measures, allowing the deployment of AsyncRAT, a potent remote access trojan. The attack begins with malicious LNK files disguised as popular animated character wallpapers, tricking users into execution. Utilizing obfuscated PowerShell scripts, the malware fetches additional payloads from remote servers while manipulating AMSI protections in memory to avoid detection. Once activated, AsyncRAT grants attackers full control over compromised systems, enabling keystroke logging, credential theft, and data exfiltration. This multi-stage attack highlights the evolving tactics of cybercriminals to circumvent traditional security defenses.