Black Hat MEA 2024 Focuses on Treyfer Algorithm in Malware
/ 4 min read
Quick take - The Black Hat MEA 2024 conference will focus on the relationship between cryptography and malware, featuring discussions on the Treyfer algorithm, a lightweight block cipher designed for educational purposes, and providing insights into implementing cryptographic techniques to enhance cybersecurity practices.
Fast Facts
- Black Hat MEA 2024 Conference: Focuses on the intersection of cryptography and malware, highlighting the use of cryptography for stealthy communication in malware development.
- Treyfer Algorithm: A lightweight block cipher designed for educational purposes, emphasizing key setup, rounds of operations, and XOR, substitution, and permutation techniques for encryption and decryption.
- Practical Implementation: Attendees will learn to implement the Treyfer encryption function using a 128-bit key, focusing on iterative processes to enhance cryptographic security.
- Common Pitfalls: Emphasizes the importance of key management, thorough testing, reliance on established cryptographic libraries, and continuous education to avoid vulnerabilities in encryption practices.
- Hands-On Learning: Encourages experimentation with the Treyfer algorithm in malware contexts, providing practical insights and tools for evaluating cryptographic effectiveness.
Black Hat MEA 2024: Cryptography and Malware Insights
The Black Hat MEA 2024 conference is poised to be a significant event for cybersecurity professionals, offering a deep dive into the intersection of cryptography and malware. This year’s focus on leveraging cryptographic techniques to enable stealthy communication within malware underscores the growing complexity of digital threats.
Key Discussions: The Treyfer Algorithm
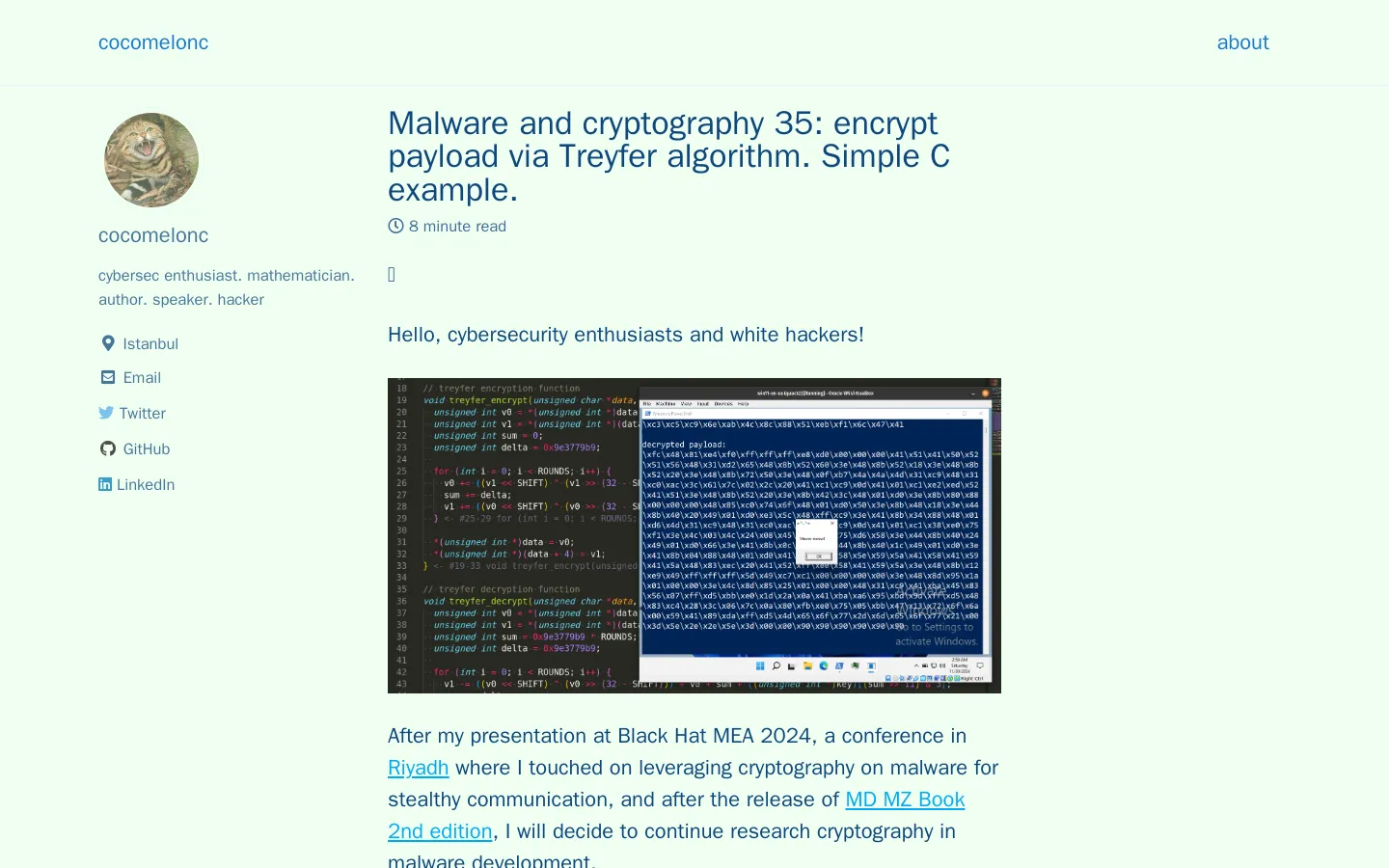
One of the central topics at the conference will be the Treyfer algorithm, a lightweight block cipher designed for educational purposes and environments with limited computational resources. This algorithm serves as an excellent entry point for attendees eager to understand cryptographic principles without requiring extensive hardware.
Participants will explore the basic steps of the Treyfer algorithm, which include key setup, rounds of operations, and the application of XOR, substitution, and permutation techniques. These processes are crucial for both encryption and decryption, providing foundational knowledge essential for implementing cryptographic techniques effectively in constrained environments.
Practical Implementation Insights
The conference will also offer practical insights into implementing the Treyfer encryption function using a 128-bit key. Attendees will focus on the encryption loop, which operates over several rounds, emphasizing the importance of iterative processes in cryptographic security. A particularly intriguing aspect is how the algorithm modifies the first half of the data during encryption by combining shifted and altered versions with round-dependent and key-dependent values. This sophisticated approach to data security could prove beneficial in various applications, including malware development.
Implications for Cybersecurity
The discussions at Black Hat MEA 2024 have far-reaching implications. As cyber threats continue to evolve, understanding advanced cryptographic methods like the Treyfer algorithm equips cybersecurity professionals with tools to combat these threats. The insights gained will be crucial for developing more resilient security measures in an increasingly complex digital ecosystem.
Best Practices for Cryptography
To maximize learning outcomes, several best practices are emphasized:
- Understand Cryptographic Basics: Familiarize yourself with fundamental principles to better grasp algorithms like Treyfer.
- Use Lightweight Algorithms: Employ lightweight block ciphers for educational purposes, especially in resource-constrained environments.
- Implement Key Setup Properly: Ensure correct division of keys into required words for effective encryption.
- Focus on Rounds for Security: Utilize multiple rounds of operations to enhance encryption strength.
Avoiding Common Pitfalls
Attendees are also cautioned against common mistakes that can undermine encryption effectiveness:
- Neglecting Key Management: Secure generation and storage of keys are vital to prevent unauthorized access.
- Overlooking Testing: Rigorous testing of encryption and decryption processes is crucial to avoid errors.
- Ignoring Security Best Practices: Rely on well-reviewed cryptographic libraries instead of custom solutions.
- Complacency in Knowledge: Stay updated with evolving cybersecurity trends and techniques.
Hands-On Learning with Treyfer
The tutorial component delves into the intricacies of the Treyfer Algorithm, guiding participants through its implementation for encrypting and decrypting payloads. This hands-on approach fosters a deeper understanding of cryptographic techniques and their application in malware development.
Participants are encouraged to experiment actively with the Treyfer algorithm, enhancing their comprehension through practical engagement. The tutorial also emphasizes testing and analysis using platforms like ANY.RUN and VirusTotal to evaluate detection rates by antivirus engines. This comprehensive approach equips learners with both theoretical knowledge and practical skills, paving the way for further exploration of cryptography’s applications.
By adhering to these guidelines and avoiding common pitfalls, individuals can improve their understanding of cryptographic systems and enhance their practical skills in implementing secure encryption solutions.
Original Source: Read the Full Article Here