CSPT Vulnerabilities in Web Applications Explored
/ 5 min read
Quick take - Recent investigations into web application security have highlighted the Critical Security Path Testing (CSPT) methodology and its associated vulnerabilities, particularly the “CSPT2CSRF: GET to POST Sink” vulnerability, emphasizing the need for developers and security professionals to effectively identify and mitigate such risks.
Fast Facts
-
CSPT Vulnerability Focus: The article highlights the “CSPT2CSRF: GET to POST Sink” vulnerability, emphasizing the need for developers to identify and mitigate such risks in web applications.
-
Eval Villain Tool: Users are encouraged to utilize the Eval Villain tool in Firefox, enabling the “Path search” feature to effectively monitor and analyze potential CSPT vulnerabilities.
-
Testing Process: The tutorial outlines a step-by-step process for testing, including logging into the CSPT playground, refreshing the page, and appending specific strings to the URL path to identify vulnerabilities.
-
Common Pitfalls: Key mistakes to avoid include not enabling the “Path search” option, ignoring source maps, and rushing through the debugging process, which can hinder effective vulnerability assessment.
-
Recommended Tools: Essential tools for addressing CSPT vulnerabilities include Eval Villain, Firefox, the CSPT Playground, and Burp Suite, each providing unique functionalities for security testing and analysis.
Unveiling CSPT Vulnerabilities in Web Applications: A Comprehensive Guide
Recent investigations into web application security have brought to light the Critical Security Path Testing (CSPT) methodology, particularly focusing on the “CSPT2CSRF: GET to POST Sink” vulnerability. This vulnerability poses significant risks if not properly addressed, making it imperative for developers and security professionals to understand how to identify and mitigate such threats.
Understanding the CSPT2CSRF Vulnerability
The CSPT2CSRF vulnerability allows attackers to exploit web applications by manipulating the transition from GET to POST requests. This can lead to unauthorized actions being performed on behalf of a user, potentially compromising sensitive data. The vulnerability underscores the need for continuous security testing and vigilance in web application development.
Engaging with the CSPT Playground
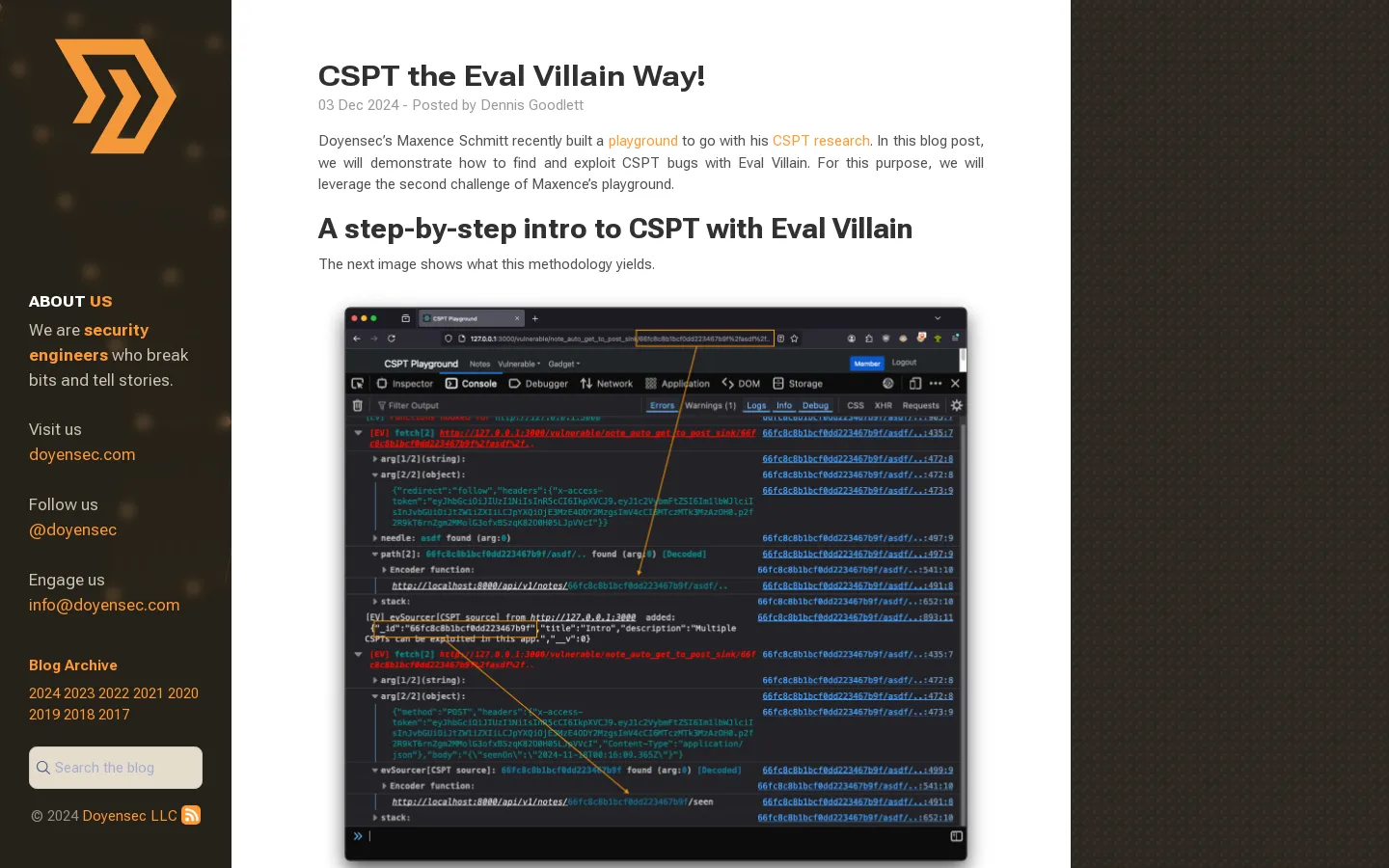
To explore this vulnerability, users are instructed to log into the CSPT playground and navigate to the “CSPT2CSRF: GET to POST Sink” page. Accessing the console is crucial, with shortcuts available for different operating systems—Ctrl+Shift+I for Linux and Command+Option+I for Mac users.
A critical step involves activating the Eval Villain tool and enabling the “Path search” feature within the console’s pop-up menu. This setup is essential for monitoring application behavior and identifying potential vulnerabilities.
Probing for Vulnerabilities
Once configured, users should refresh the page to observe network calls made using the specified path. This process can reveal important information about how the application responds to potential vulnerabilities. By appending a specific string to the path and refreshing again, users can further probe for CSPT primitives, gaining insight into the application’s security posture.
Implications for Web Application Security
The ability to identify and exploit CSPT vulnerabilities highlights the importance of ongoing security testing in web applications. As cyber threats evolve, developers must remain vigilant and proactive in implementing security measures to protect sensitive data and maintain user trust. Understanding tools like Eval Villain and methodologies such as CSPT empowers security teams to better defend against potential attacks.
Best Practices for Using Eval Villain
To effectively utilize Eval Villain, it is recommended to use Firefox with Eval Villain installed. Enabling the “Path search” feature is crucial as it enhances the ability to pinpoint potential CSPT vulnerabilities by including URL paths as sources.
Adding a specific string to the URL path during testing can simplify determining whether a website is susceptible to CSPT attacks. Additionally, activating the global “evSourcer” option in Eval Villain allows users to ingest responses from CSPT requests into Eval Villain’s source bank, facilitating comprehensive data analysis.
Common Pitfalls in Debugging
Users should be mindful of several key areas that can impact their debugging experience significantly. Not enabling the “Path search” option can leave critical security flaws undetected. Ignoring source maps may obscure vital debugging information, complicating code inspection.
Overlooking object types during debugging is another common oversight. By default, Eval Villain focuses on strings, which means essential data may be missed if object inspection is not enabled. Rushing through debugging processes can also lead to missed breakpoints or incorrect outcomes.
Exploring Client-Side Parameter Tampering (CSPT)
Participants are introduced to fundamental aspects of CSPT vulnerabilities, equipping them with knowledge necessary for recognizing these security issues. Hands-on demonstrations guide users through manipulating URL paths and testing for vulnerabilities, enhancing their skills in vulnerability assessment.
Capturing and analyzing responses from CSPT requests provides insights into potential exploits. This analytical approach fosters a deeper understanding of security landscapes, empowering users to devise robust security measures.
Tools and Resources for Addressing CSPT Vulnerabilities
Several tools are recommended for effectively identifying and exploiting CSPT vulnerabilities:
- Eval Villain: A powerful JavaScript function designed for identifying CSPT vulnerabilities.
- Firefox: A robust browser essential for running Eval Villain.
- CSPT Playground: A vulnerable web application within a Docker environment for safe testing.
- Burp Suite: A leading web application security testing tool with advanced features like Bambda search.
By leveraging these tools and resources, individuals can enhance their understanding and proficiency in addressing CSPT vulnerabilities, ensuring a well-rounded approach to both learning and practical application.