Tool Released for Bypassing Windows Credential Guard
/ 3 min read
Quick take - A new tool called NativeBypassCredGuard has been released on GitHub, allowing users to bypass the Credential Guard feature in Windows systems, which raises concerns about the security of user credentials stored in memory.
Fast Facts
-
Tool Release: NativeBypassCredGuard, a new tool on GitHub, allows users to bypass Windows Credential Guard, raising security concerns about credential storage.
-
Functionality: The tool manipulates the WDigest.dll file to disable Credential Guard protections, enabling user credentials to be stored in cleartext in memory.
-
Technical Steps: Users must identify a specific pattern in WDigest.dll, calculate memory addresses, and patch variables to enable plaintext credential storage.
-
Security Risks: Utilizing this tool poses significant risks, including unauthorized access to sensitive information, highlighting vulnerabilities in Windows security protocols.
-
Caution Advised: Users are urged to verify the integrity of WDigest.dll, test in controlled environments, and ensure they have the necessary privileges to avoid potential security threats.
New Tool Emerges for Bypassing Credential Guard in Windows
A newly released tool, NativeBypassCredGuard, has surfaced on GitHub, raising alarms within the cybersecurity community. This tool offers a method to bypass the Credential Guard feature in Windows systems, potentially compromising the security of user credentials stored in memory.
Understanding NativeBypassCredGuard
NativeBypassCredGuard is designed to manipulate the WDigest.dll file, a critical component in Windows security architecture. Credential Guard typically protects user credentials by storing them securely; however, this tool provides a way to disable those protections. The tool can be accessed via its GitHub repository.
How the Tool Works
To utilize NativeBypassCredGuard effectively, users must follow a series of technical steps:
-
Pattern Identification: Users begin by identifying a specific pattern within the WDigest.dll file on disk. The pattern required is “39 ?? ?? ?? ?? 00 8b ?? ?? ?? ?? 00”.
-
Memory Address Calculation: Once identified, users calculate the memory addresses associated with this pattern within the WDigest.dll file.
-
Patching Variables: Critical variables within WDigest.dll are then patched. Specifically,
g_fParameter_UseLogonCredentialis set to 1 andg_IsCredGuardEnabledto 0. -
Credential Storage in Cleartext: After patching, the tool ensures that user credentials are stored in cleartext in memory, effectively bypassing Credential Guard protections.
Implications for User Security
The release of NativeBypassCredGuard underscores potential vulnerabilities in Windows security protocols. By enabling plaintext storage of user credentials, it poses significant risks such as unauthorized access to sensitive information. Users are advised to exercise caution when considering the use of such tools due to the inherent security threats they introduce.
Technical Considerations
NativeBypassCredGuard is engineered to circumvent Credential Guard protections by patching the WDigest.dll file. This allows for plaintext credential storage in memory—a key aspect of its functionality. Users must choose between C# and C++ implementations based on their development environment needs, as each version has unique characteristics.
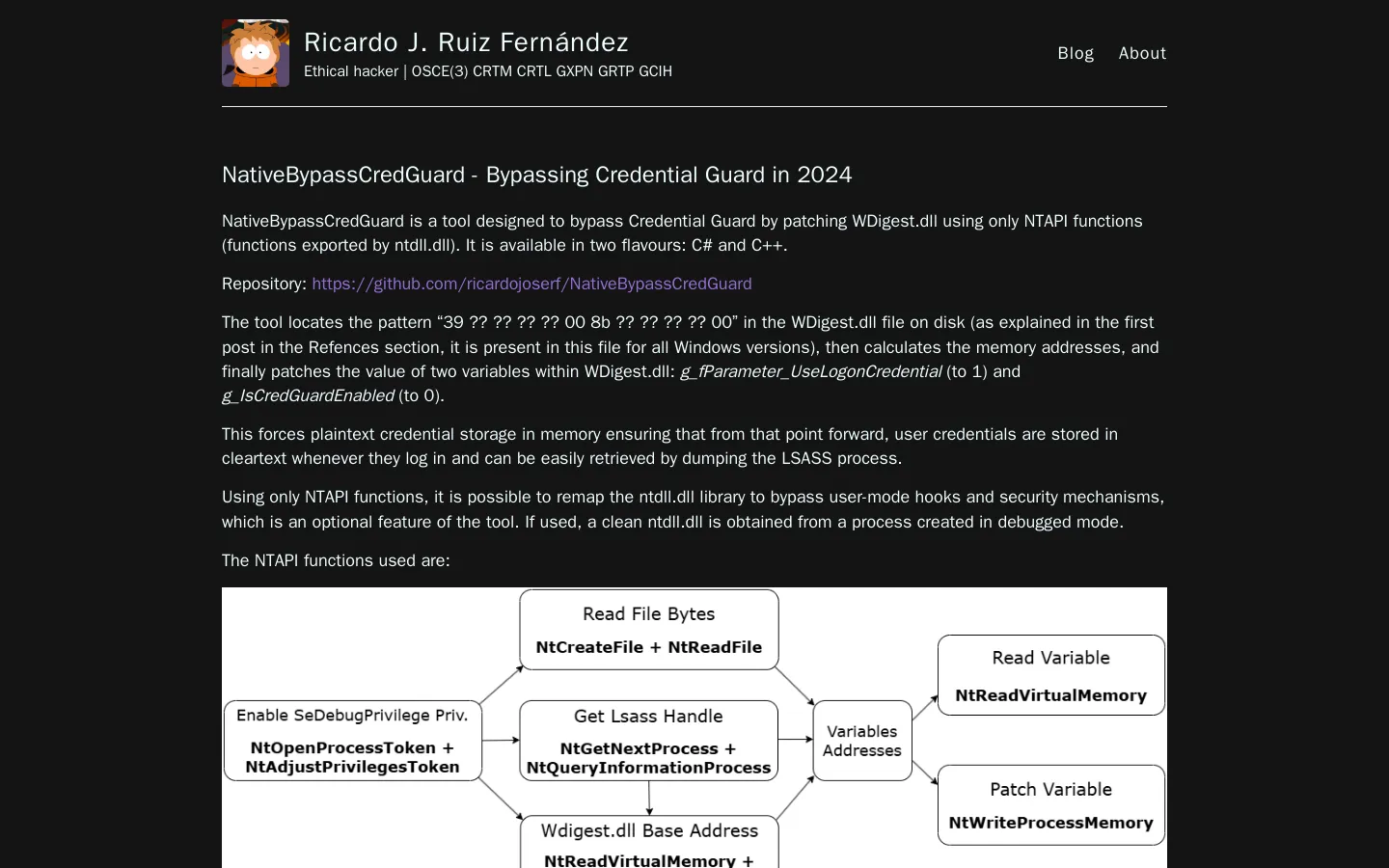
The tool’s effectiveness relies on modifying key variables within WDigest.dll. By setting g_fParameter_UseLogonCredential to 1 and g_IsCredGuardEnabled to 0, it enables plaintext credential storage. Additionally, NativeBypassCredGuard utilizes NTAPI functions to interact seamlessly with system processes and files, bypassing user-mode hooks and other security mechanisms.
Privilege Requirements and Best Practices
Enabling SeDebugPrivilege is crucial for using NativeBypassCredGuard effectively. Functions like NtOpenProcessToken and NtAdjustPrivilegesToken are employed to elevate privileges and access protected processes necessary for execution.
Users should verify the integrity of WDigest.dll before proceeding with any modifications. Testing in a controlled environment—such as a virtual machine—is recommended to mitigate risks associated with damaging production systems or losing valuable data.
Conclusion
The emergence of tools like NativeBypassCredGuard highlights ongoing challenges in maintaining robust cybersecurity defenses against evolving bypass techniques. Users must remain vigilant about potential vulnerabilities and consider the broader implications of utilizing such tools within their systems.