Windows Security Vulnerabilities Related to False File Immutability
/ 5 min read
Quick take - The article discusses the vulnerabilities associated with “False File Immutability” in Windows operating systems, emphasizing the security risks it poses, particularly regarding unauthorized access to sensitive data, and advocates for responsible disclosure practices among cybersecurity professionals to mitigate these risks.
Fast Facts
-
False File Immutability Risks: The misconception that files remain unchanged without the FILE_SHARE_WRITE mode can lead to significant security vulnerabilities in Windows, allowing unauthorized access to sensitive data.
-
Vulnerability Exploitation: Attackers can exploit the assumption of immutability, particularly in remote file access scenarios, to manipulate or retrieve confidential information undetected.
-
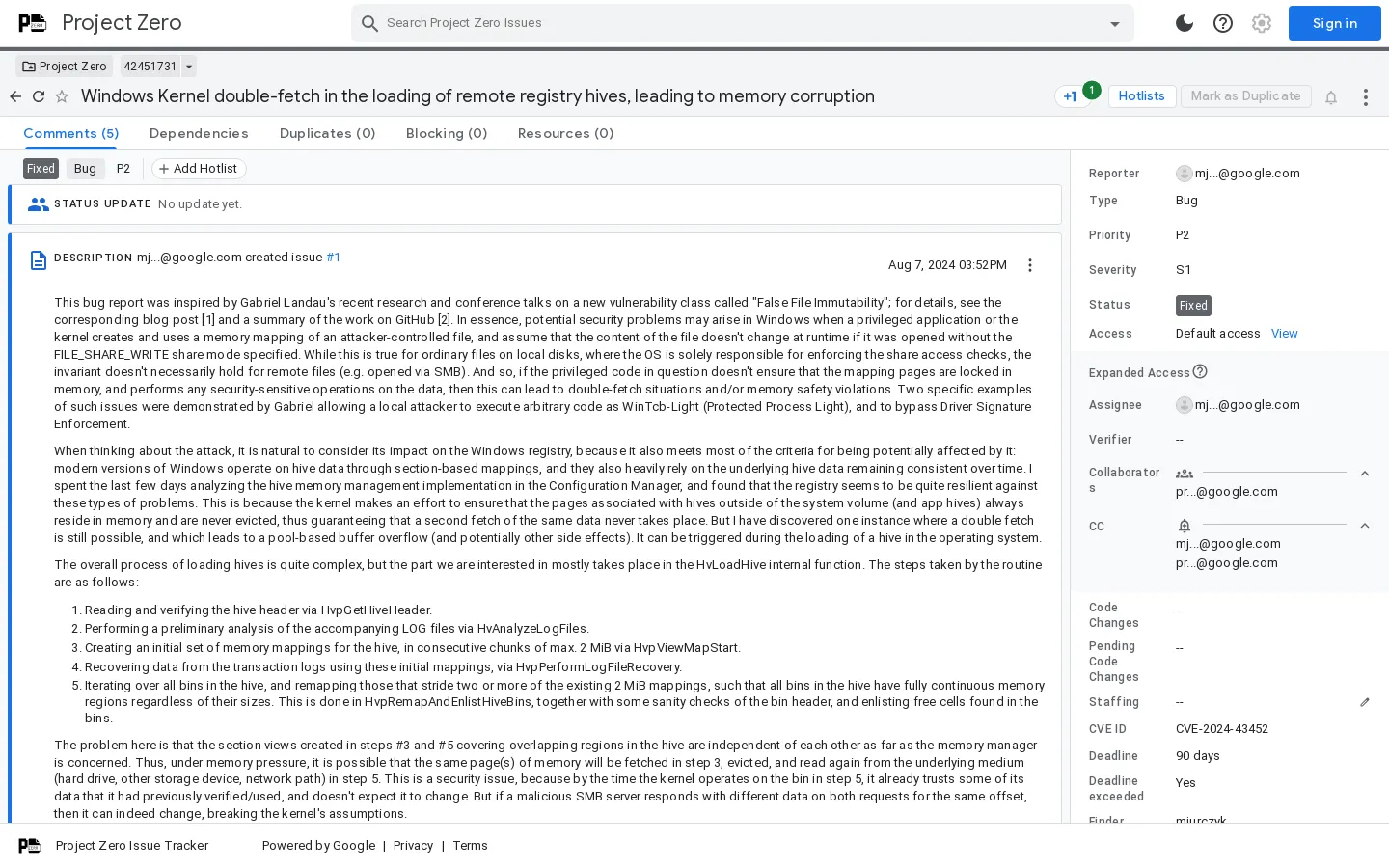
Registry Vulnerabilities: The tutorial emphasizes the need to analyze the Windows registry’s resilience against double-fetch vulnerabilities, which can compromise system security.
-
Responsible Disclosure Advocacy: Cybersecurity professionals are encouraged to adopt responsible disclosure practices to effectively manage and report vulnerabilities, minimizing risks before exploitation occurs.
-
Best Practices for Mitigation: Key steps include understanding the context of vulnerabilities, implementing strict access controls, utilizing cryptographic hashing, and regularly updating systems to enhance security against false file immutability.
Understanding False File Immutability and Its Security Implications in Windows Environments
Recent discussions within the cybersecurity community have brought to light critical vulnerabilities associated with “False File Immutability” in Windows operating systems. This phenomenon poses significant security risks, particularly concerning memory mappings of files and the management of registry data. As experts delve into these issues, there is a growing emphasis on responsible disclosure practices to manage the implications of these vulnerabilities effectively.
The Concept of False File Immutability
False File Immutability refers to the erroneous assumption that a file’s content remains unchanged when accessed without the FILE_SHARE_WRITE mode. This misconception can lead to severe security vulnerabilities in Windows environments, as it can allow unauthorized access to potentially volatile data. When file content is presumed immutable, attackers could exploit this oversight to manipulate or retrieve sensitive information without detection, thereby compromising the integrity and confidentiality of the system.
Vulnerabilities Arising from False Assumptions
A primary focus of recent discussions is on specific vulnerabilities that can arise from this false assumption, particularly in scenarios involving remote file access. The belief that files are immutable when they are not can lead to unauthorized data manipulation or exposure. This oversight can be especially dangerous when dealing with sensitive or confidential information, as it opens up potential attack vectors for malicious actors.
Registry Resilience and Double-Fetch Vulnerabilities
Another significant aspect of the analysis is the assessment of the Windows registry’s resilience against exploitation through double-fetch vulnerabilities. Experts are examining how memory management associated with hive data can be manipulated and the potential consequences of such vulnerabilities on overall system security. This analysis is crucial for understanding how attackers might exploit these weaknesses to gain unauthorized access or control over a system.
Responsible Disclosure Practices
A crucial takeaway from these discussions is the advocacy for responsible disclosure practices among cybersecurity professionals. Establishing a clear timeline for reporting identified vulnerabilities and understanding the ramifications of public disclosure are essential steps in mitigating risks. Effective communication and responsible handling of vulnerabilities help ensure that they can be addressed before being exploited by malicious actors.
Implications for Windows Environments
The implications of false file immutability and the associated vulnerabilities are far-reaching. With increasing reliance on Windows environments for both personal and organizational data management, understanding these security risks is vital for safeguarding sensitive information. The focus on responsible disclosure is equally important, as it helps ensure that vulnerabilities can be addressed before they are exploited by malicious actors.
Essential Steps for Mitigation
-
Understand the Context: Recognize that false file immutability arises when files meant to be immutable can be altered due to improper restrictions or oversights in permission settings.
-
Implement Strict Access Controls: Enforce strict access control measures by properly configuring file permissions to ensure only authorized users can modify or delete files.
-
Utilize Cryptographic Hashing: Incorporate cryptographic hashing to detect any modifications by comparing current hash values against originals.
-
Regularly Update and Patch Systems: Keep software and systems updated to prevent vulnerabilities, including false file immutability.
By following these steps, organizations can significantly enhance their defenses against the risks presented by false file immutability, ultimately leading to a more secure and resilient system.
Best Practices for Addressing Vulnerabilities
Maintaining thorough documentation for all encountered vulnerabilities is crucial. This should include detailed descriptions, potential impacts, and mitigation steps. Regular updates create a comprehensive knowledge base for future reference. Additionally, fostering collaboration among team members improves response strategies by encouraging open discussions about vulnerabilities.
Leveraging automated tools for vulnerability scanning streamlines identification processes, allowing teams to focus on critical issues. Coupled with regular training and workshops, these tools enhance capabilities in managing security vulnerabilities effectively.
Common Pitfalls and Proactive Management
Users often underestimate the risk associated with false file immutability, assuming their files are secure simply because they are marked as immutable. This misconception leads to a false sense of security, making users less vigilant about monitoring file integrity and potential unauthorized access.
Neglecting appropriate access controls allows malicious actors to bypass protections even if files are marked as immutable. Ensuring rigorous user access management safeguards against unauthorized alterations.
Failing to regularly update software leaves users exposed to exploits taking advantage of this issue. Keeping systems up-to-date with security patches is vital for maintaining file integrity.
Recommended Tools and Resources
-
Impacket: A suite of Python classes aiding in network protocol manipulation, valuable for testing network-related applications.
-
Windows Debugging Tools (WinDbg): A powerful toolset for debugging Windows applications, ideal for analyzing application behavior related to file integrity.
-
GitHub Repository by Gabriel Landau: Contains scripts and documentation related to “False File Immutability,” providing practical resources for developers.
-
Elastic Security Labs Blog Post: Offers an in-depth analysis of the vulnerability with case studies and best practices for remediation.
By utilizing these tools and resources, security professionals can better navigate the complexities of “False File Immutability” and enhance their defensive measures against potential exploits.