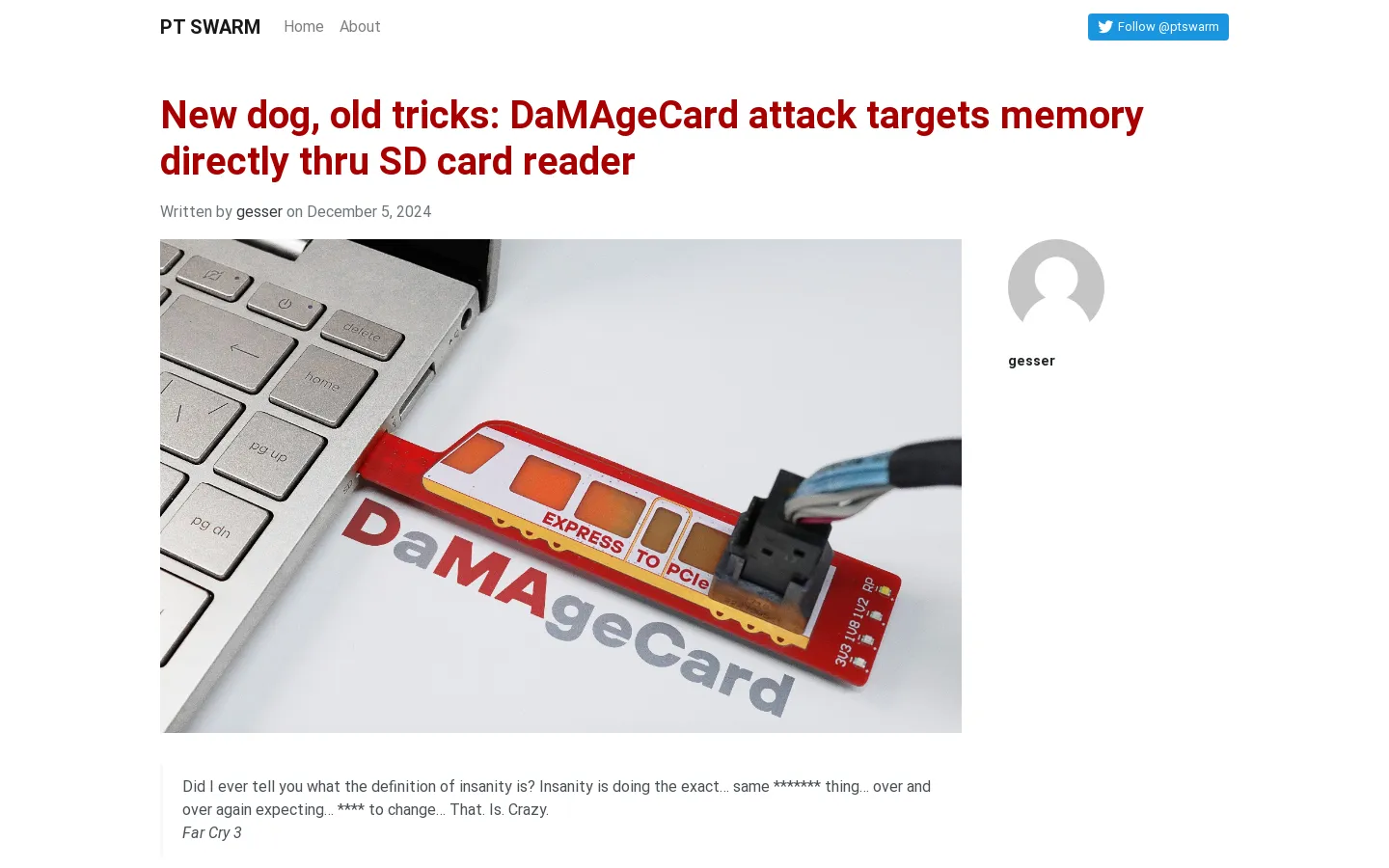
SD Express Technology Faces DMA Attack Vulnerabilities
/ 4 min read
Quick take - Experts have analyzed the SD Express standard, highlighting its significant speed improvements for data transfer while also raising concerns about security vulnerabilities related to direct memory access (DMA) attacks.
Fast Facts
-
SD Express Overview: The SD Express standard enhances data transfer speeds for SD cards, benefiting both consumers and professionals, but raises security concerns related to direct memory access (DMA) vulnerabilities.
-
Security Risks: The tutorial highlighted potential attack vectors, particularly DMA attacks, which exploit direct access to memory, emphasizing the need for robust security measures to protect against these threats.
-
Importance of IOMMU: Implementing Input-Output Memory Management Unit (IOMMU) technology is crucial for isolating DMA requests and preventing unauthorized access to system memory, thereby enhancing security.
-
Research and Development: Ongoing academic research is focused on understanding DMA vulnerabilities and developing innovative solutions to improve system security, highlighting the need for continuous vigilance.
-
Proactive Security Measures: Organizations are encouraged to adopt best practices, such as regular training on cybersecurity awareness and implementing stringent access controls, to mitigate risks associated with new technologies and DMA capabilities.
SD Express: Balancing Speed and Security in the Face of DMA Threats
In the rapidly evolving world of data storage technology, the SD Express standard has emerged as a significant advancement, promising enhanced data transfer speeds that cater to both consumer and professional needs. However, alongside these technological strides come pressing security concerns, particularly regarding Direct Memory Access (DMA) attacks. Recent analyses have highlighted these vulnerabilities, urging stakeholders to prioritize robust security measures.
The Promise of SD Express
SD Express represents a leap forward in Secure Digital (SD) card technology, offering substantial improvements in data transfer rates. This new standard integrates PCIe and NVMe interfaces, enabling faster and more efficient data access compared to its predecessors. Such advancements are particularly appealing for applications requiring rapid data processing, such as high-resolution video recording and complex computational tasks.
Despite these benefits, the integration of advanced interfaces also introduces potential security risks. The increased speed and efficiency of SD Express can inadvertently expand the attack surface for malicious actors seeking to exploit system vulnerabilities.
Understanding DMA Attacks
DMA attacks exploit the capability of certain devices to directly access system memory without CPU intervention. While this feature enhances performance by offloading tasks from the CPU, it also poses significant security risks if not properly managed. Attackers can leverage tools like PCILeech to read or write system memory, bypassing traditional software-based defenses.
The tutorial on SD Express underscored how these vulnerabilities could be exploited in modern devices. Experts demonstrated practical examples of DMA attacks, highlighting the need for comprehensive security protocols to protect against unauthorized memory access.
Mitigating Security Risks
To counteract the threats posed by DMA attacks, several strategies have been recommended:
-
Implementation of IOMMU: The Input-Output Memory Management Unit (IOMMU) is a critical defense mechanism that isolates DMA requests from peripheral devices, preventing unauthorized memory access. Its adoption is becoming increasingly common in environments handling sensitive data.
-
Regular Firmware Updates: Keeping system firmware up-to-date is essential in addressing known vulnerabilities. Manufacturers must ensure that their devices are equipped with the latest security patches to mitigate potential exploits.
-
Enhanced Access Controls: Implementing stringent access controls can significantly reduce the risk of unauthorized device connections. Organizations should enforce policies that limit peripheral device usage and monitor for unusual activity.
-
Security Awareness Training: Educating users about the risks associated with peripheral devices is crucial. Regular training sessions can help individuals recognize potential threats and adopt security-first behaviors in their daily operations.
Looking Ahead
As SD Express technology continues to gain traction, maintaining a dual focus on speed and security is imperative. The findings from recent analyses serve as a reminder for manufacturers and consumers alike to remain vigilant about device security. The unchecked vulnerabilities associated with DMA attacks could lead to severe data breaches and exploitation.
In response to these challenges, ongoing education and awareness will be vital in navigating the intersection of innovation and security within digital storage realms. By staying informed about emerging threats and implementing proactive measures, stakeholders can safeguard their systems while reaping the benefits of advanced data transfer technologies.
Next Steps
To further explore this topic, consider delving into key areas such as:
- Understanding DMA and PIO Models: Gain insights into how these models operate and their implications for data transfer efficiency.
- Exploring Bus Mastering DMA: Learn about this technique’s impact on system performance and its interaction with other components.
- Evaluating SD Express Security: Examine integrated security features and best practices for protecting sensitive information.
- Conducting Practical Experiments: Simulate scenarios involving DMA and SD Express to gather real-world insights into performance metrics and vulnerabilities.
By following these steps, you can enhance your understanding of peripheral device security and improve your systems’ overall security posture against potential DMA attacks.