Proactive Measures for Enhancing Data Security Identified
/ 4 min read
Quick take - A recent tutorial for IT professionals emphasized the critical need for organizations to address data security risks associated with various storage methods and introduced effective strategies and tools, such as NodeZero, to enhance data protection and mitigate vulnerabilities.
Fast Facts
-
Growing Data Security Risks: Organizations face increasing vulnerabilities in data storage methods, necessitating a comprehensive understanding of potential risks associated with local files, file shares, and cloud backups.
-
Real-World Attack Scenarios: The tutorial highlighted how cybercriminals exploit weaknesses in data storage systems, emphasizing the need for robust security measures to prevent unauthorized access.
-
NodeZero Capabilities: NodeZero was showcased as a powerful tool for identifying sensitive data and rogue credentials, aiding organizations in strengthening their defenses against data breaches.
-
Proactive Security Measures: The session advocated for the implementation of automated tools and continuous monitoring to anticipate and prevent cybersecurity threats, rather than merely reacting to them.
-
Best Practices for Data Management: Organizations are encouraged to adopt strong access controls, encryption, regular audits, and employee training to enhance their security posture and protect sensitive information effectively.
Enhancing Data Security Through Proactive Measures
In an era where digital platforms are integral to storing sensitive information, organizations face mounting pressure to address data security risks. A recent tutorial aimed at IT professionals and organizational leaders shed light on critical vulnerabilities in data storage, emphasizing the need for proactive measures. The session highlighted the capabilities of NodeZero, a tool designed to fortify defenses against potential breaches.
Understanding the Risks
The tutorial began by underscoring the growing threats associated with various data storage methods, including local files, file shares, and cloud backups. As cyber threats evolve, sensitive data often remains exposed, making it imperative for organizations to recognize the vulnerabilities inherent in their data management practices.
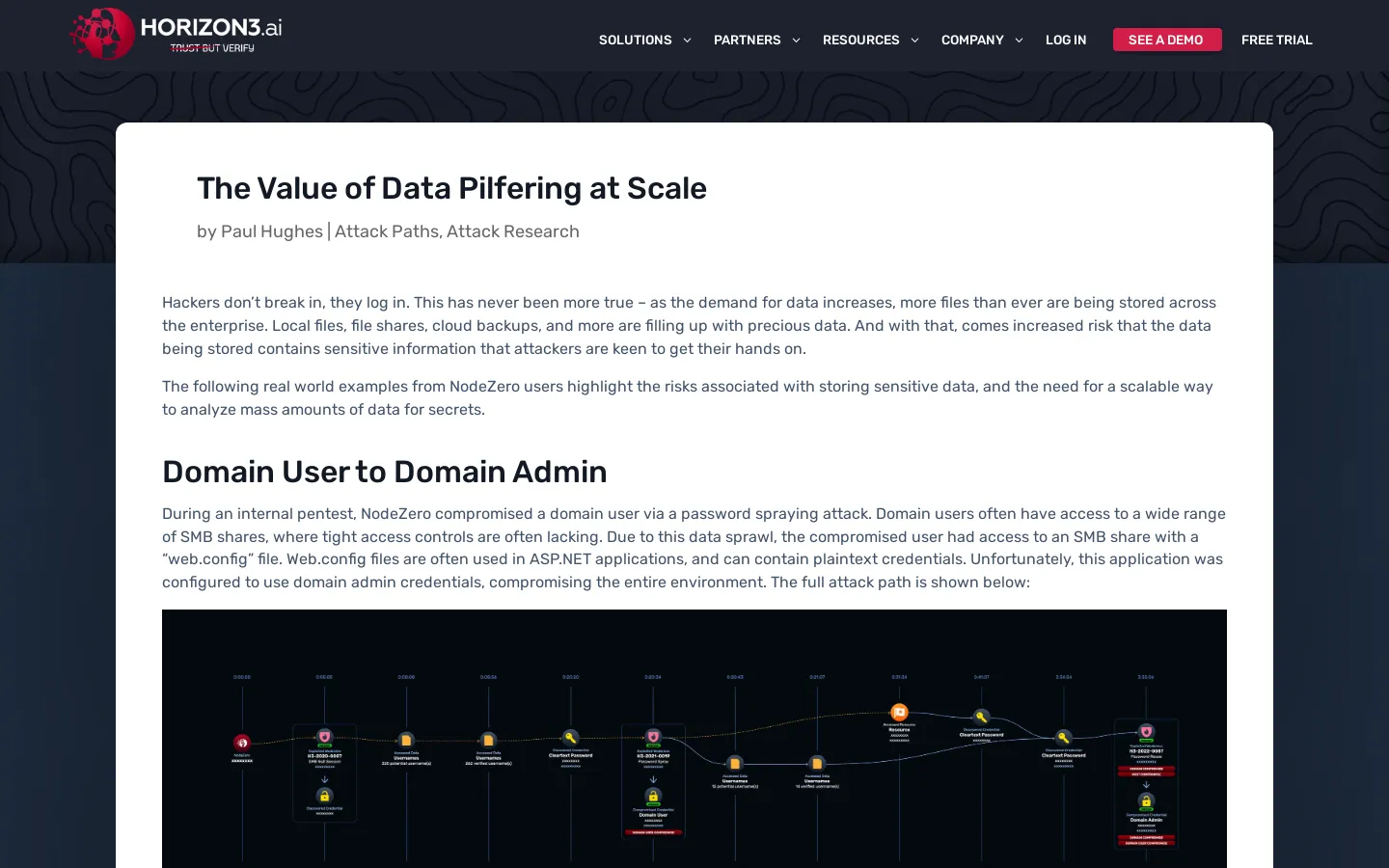
Real-world attack scenarios were presented to illustrate how malicious actors exploit these vulnerabilities. These examples served as stark reminders of the consequences of inadequate security measures, demonstrating how unauthorized access and privilege escalation can occur when systems are not properly secured.
NodeZero: A Key Player in Data Security
A significant portion of the tutorial was dedicated to showcasing NodeZero’s capabilities. This tool is adept at identifying and analyzing sensitive data across multiple sources, enabling organizations to uncover rogue credentials that could compromise security. By efficiently managing data sprawl, NodeZero helps organizations strengthen their defenses against data breaches.
The session advocated for the implementation of proactive security measures using automated tools like NodeZero. Such tools empower organizations not only to react to cybersecurity threats but also to anticipate and prevent them.
Implications for Organizations
The insights shared during the tutorial have far-reaching implications for organizations across various sectors. With data breaches becoming increasingly common, robust security protocols are more crucial than ever. By highlighting risks and promoting proactive measures, organizations can better protect their sensitive information.
Advanced tools like NodeZero offer promising avenues for improving data security management. As organizations navigate complex digital environments, leveraging such technologies will be critical in safeguarding against evolving cyber threats.
Actionable Steps for Enhanced Security
In light of these findings, organizations must take proactive steps to enhance their security posture:
-
Conduct Internal Penetration Testing: Regular testing is essential to identify vulnerabilities that could be exploited by malicious actors. Simulating real-world attacks within the organization’s network helps uncover weaknesses before they are targeted.
-
Identify and Analyze Sensitive Files: Conduct a thorough inventory of sensitive files, including personal data and proprietary information. Understanding where sensitive data resides enables better protection strategies and ensures compliance with privacy regulations.
-
Assess Credential Storage Practices: Evaluate how credentials are stored and managed. Ensure strong encryption methods are in place and replace outdated practices with industry-standard solutions to reduce unauthorized access risks.
-
Implement Scalable Solutions for Continuous Monitoring: Adopt scalable solutions that provide continuous monitoring of systems and networks. This allows real-time detection of anomalies and swift responses to potential threats.
By following these steps, organizations can significantly improve their security measures and better protect sensitive data from evolving threats.
Best Practices for Data Management
To further enhance understanding and efficiency in managing sensitive data:
- Implement robust access controls to ensure only authorized personnel have access.
- Utilize encryption for both data at rest and in transit.
- Conduct regular security audits to identify weaknesses.
- Train employees on data security protocols to foster a culture of security awareness.
- Establish clear data handling policies and incident response plans.
Addressing common pitfalls such as weak passwords or unsecured networks can also bolster defenses against cyber threats.
Leveraging Tools for Effective Data Security
Several tools can aid organizations in managing and securing sensitive information effectively:
- NodeZero: Specializes in identifying network vulnerabilities, allowing proactive risk management.
- AWS Identity and Access Management (IAM): Essential for managing access within Amazon Web Services.
- Data Loss Prevention (DLP) Solutions: Monitor and protect sensitive data from unauthorized access.
- Security Information and Event Management (SIEM) Systems: Provide real-time analysis of security alerts for effective incident response.
By leveraging these tools, organizations can strengthen their data security strategies amidst an increasingly complex threat landscape.