Ultralytics Machine Learning Package Faces Security Vulnerability
/ 5 min read
Quick take - A recent security breach in the Ultralytics machine learning package has exposed vulnerabilities in software development workflows, particularly within GitHub Actions, prompting an analysis of the attack, incident response measures, and recommendations for improving future security practices.
Fast Facts
-
Security Breach Overview: A recent breach in the Ultralytics machine learning package exposed vulnerabilities in GitHub Actions workflows, allowing unauthorized code execution through insecure triggers and template injection flaws.
-
Incident Response Actions: Immediate measures included removing malicious releases and emphasizing the need for secure coding practices to prevent future attacks.
-
Detection Improvement Needs: The incident highlighted the necessity for enhanced detection mechanisms in GitHub workflows, particularly for complex composite actions that are harder to monitor.
-
Best Practices for Security: Key recommendations include updating dependencies, implementing access controls, conducting regular audits, and educating staff on security best practices.
-
Tools for Vulnerability Management: Resources like GitHub Actions Security Scanner, Sigstore, OWASP Dependency-Check, and SAST tools are essential for identifying and mitigating vulnerabilities in software development processes.
Security Breach in Ultralytics Machine Learning Package: A Comprehensive Analysis
A recent security breach in the Ultralytics machine learning package has spotlighted significant vulnerabilities within software development workflows, particularly those utilizing GitHub Actions. This incident has prompted a detailed examination of the attack’s execution, the exploited vulnerabilities, and the subsequent steps taken to respond and enhance future detection capabilities.
Understanding the Vulnerability
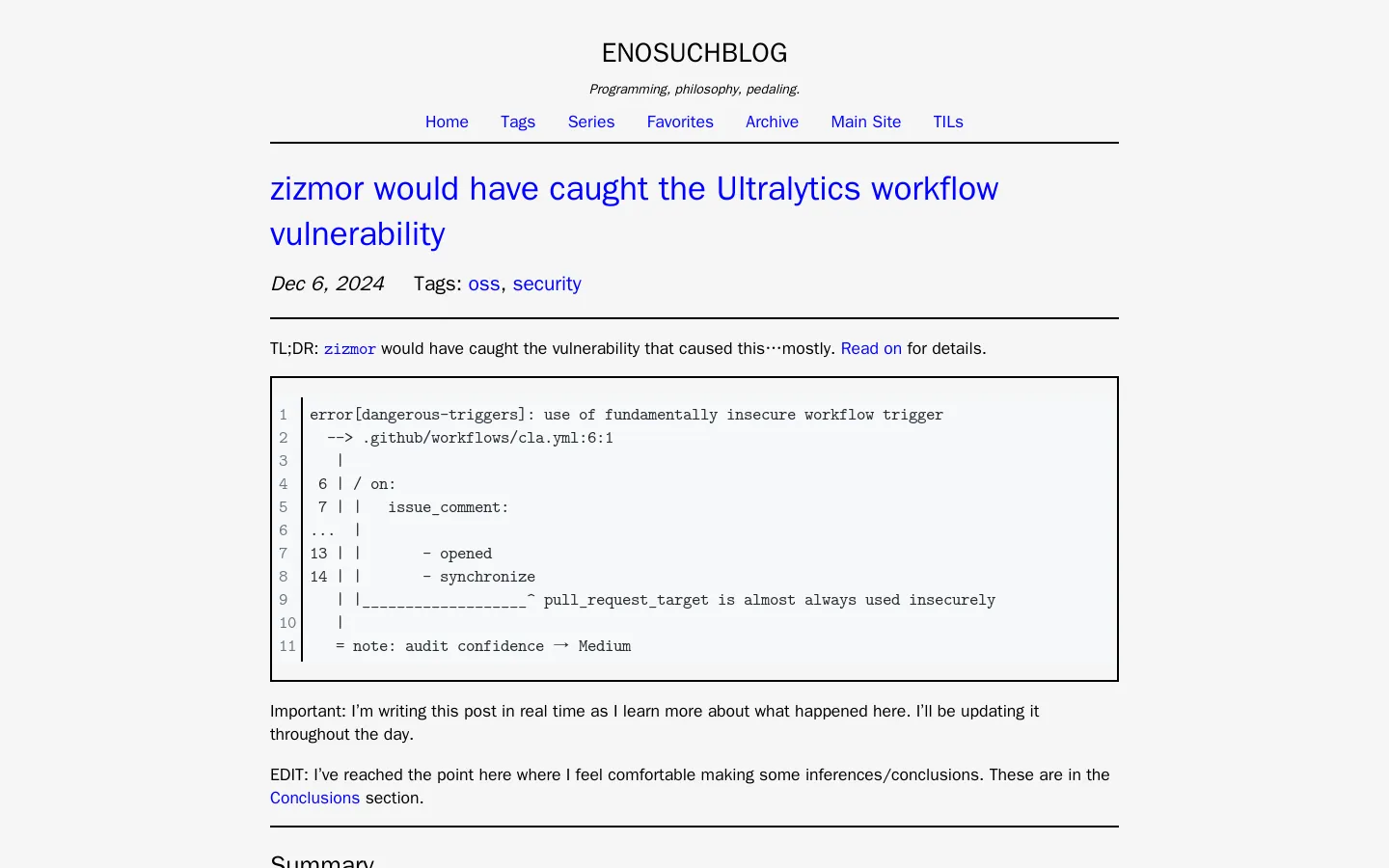
The breach in the Ultralytics package underscores critical security flaws that enabled attackers to execute malicious code. The attack leveraged specific vulnerabilities within the GitHub Actions workflow, including insecure triggers and template injection flaws. These weaknesses allowed unauthorized code execution, posing a severe threat to the software package’s integrity and its users.
Workflow Analysis
Central to this incident was the GitHub Actions workflow configuration, which permitted unverified code execution. The analysis highlights the necessity of scrutinizing workflow configurations to identify exploitable insecure triggers. Template injection vulnerabilities were particularly alarming, as they could be manipulated to execute arbitrary code within the workflow environment, compromising the entire system.
Incident Response
In response to the breach, immediate actions were taken to identify and mitigate the attack. This included removing malicious releases that had infiltrated the package. The incident served as a wake-up call for implementing secure coding practices. Organizations are urged to adopt stringent security measures to fortify their development environments against similar attacks in the future.
Detection Improvement
Looking forward, this incident emphasizes the need for enhanced detection mechanisms to identify similar vulnerabilities within GitHub workflows. By focusing on composite actions, often more complex and difficult to monitor, developers can create robust systems better equipped to withstand potential exploits. Improving detection capabilities will be crucial in preventing similar breaches and ensuring the continued security of machine learning tools and other software packages.
Implications
The Ultralytics security breach serves as a critical reminder of potential vulnerabilities in modern software development practices. It stresses the importance of secure workflow configuration and continuous improvement in detection and response strategies. As software development evolves, developers and organizations must prioritize security to protect their assets and maintain user trust.
Essential Steps for Mitigating Vulnerabilities
To address these concerns, here are four essential steps outlined from a tutorial regarding the Ultralytics workflow vulnerability:
-
Update Dependencies: Regularly updating libraries and frameworks can mitigate vulnerabilities arising from outdated code. Users should check for updates regularly and apply them promptly for maximum security.
-
Implement Access Controls: Establish robust access controls by restricting system access to authorized personnel only. Role-based permissions can better protect sensitive data and workflows from potential exploitation.
-
Conduct Regular Audits: Routine security audits are crucial for identifying potential vulnerabilities before they can be exploited. Schedule regular reviews of systems and workflows to spot any anomalies or security gaps.
-
Educate and Train Staff: Empower employees with knowledge about potential threats and safe operating procedures through regular training sessions. This enhances an organization’s overall security posture by keeping everyone informed about the latest security developments.
Best Practices for Software Security
Enhancing understanding and efficiency in dealing with software security involves several best practices:
-
Automate Security Testing: Integrate automated security testing tools within your CI/CD pipeline to detect vulnerabilities early in development.
-
Implement Dependency Management: Regularly update dependencies using tools that scan for known vulnerabilities in third-party libraries.
-
Use Least Privilege Principles: Limit access rights for users and systems to minimize potential breach impacts.
-
Conduct Regular Security Audits: Schedule periodic audits of CI/CD processes to identify weaknesses and ensure compliance with security standards.
-
Educate Your Team: Provide ongoing training for development teams to recognize and respond effectively to security threats.
By following these best practices, organizations can significantly reduce security breach risks while enhancing their software development processes’ integrity.
Tools and Resources for Enhanced Security
Developers can leverage various tools and resources to understand and mitigate vulnerabilities similar to those encountered in the Ultralytics incident:
-
GitHub Actions Security Scanner (e.g., Zizmor): Automatically scans code for vulnerabilities during CI/CD processes, allowing early risk identification.
-
Sigstore: An open-source project that improves software supply chain security by enabling developers to sign software artifacts.
-
OWASP Dependency-Check: Identifies known vulnerabilities in project dependencies, providing detailed reports on potential risks.
-
Static Application Security Testing (SAST) Tools: Analyze source code for vulnerabilities without executing programs, detecting flaws early in development.
By leveraging these resources, developers can build more secure applications while maintaining a robust security posture against vulnerabilities akin to those highlighted in the Ultralytics incident.