Cybersecurity Tutorial Focuses on Honeypot Data Analysis
/ 5 min read
Quick take - A new tutorial has been developed to help cybersecurity professionals identify anomalous activity in honeypot data, focusing on unusual command execution patterns, potential DDoS indicators, and cryptocurrency-related activities, while also promoting the use of advanced data analysis tools.
Fast Facts
- A new tutorial aims to enhance cybersecurity by teaching professionals to identify anomalous activity in honeypot data, focusing on command execution patterns and DDoS indicators.
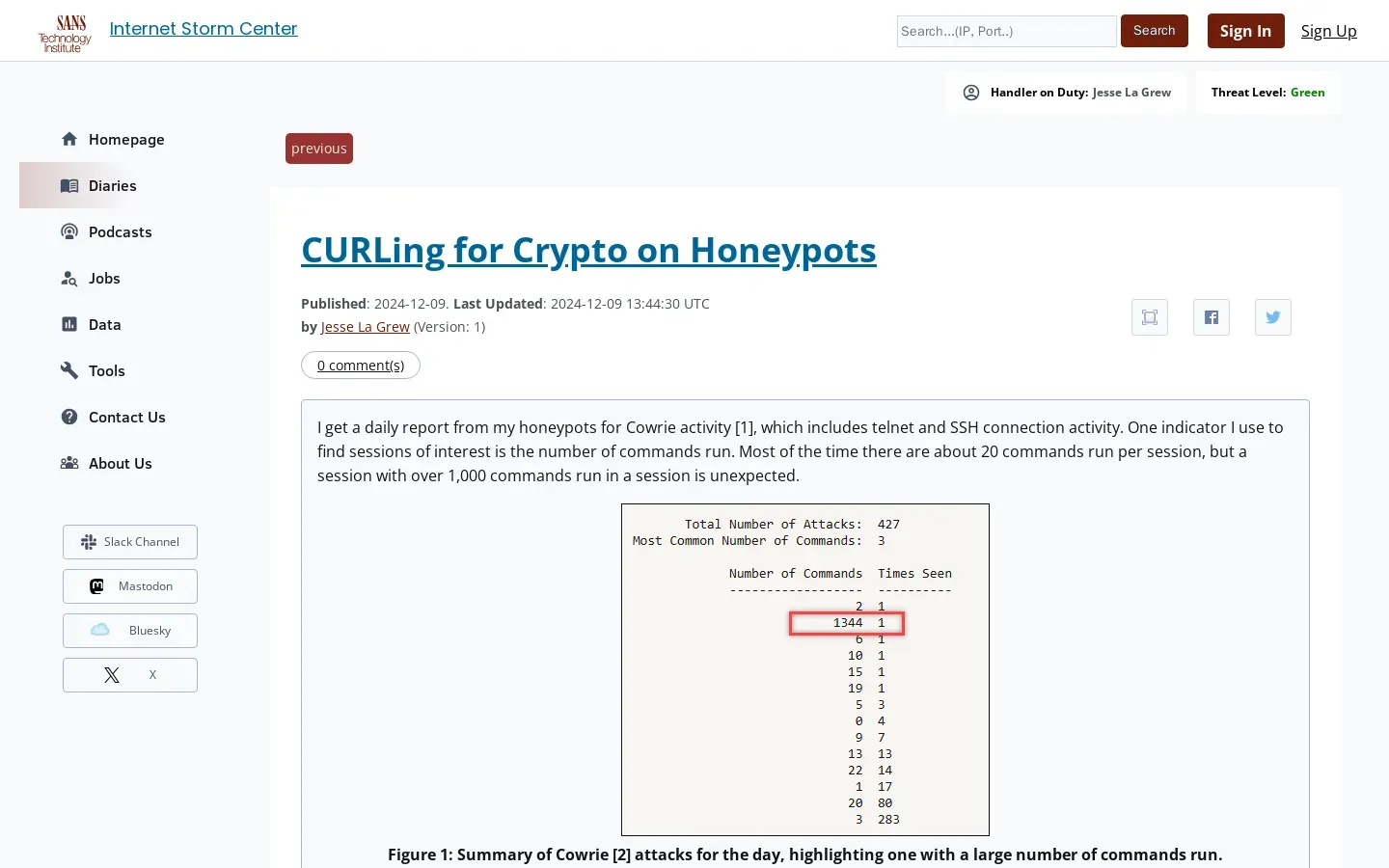
- Key objectives include detecting excessive command usage (over 1,000 commands) and analyzing repeated curl requests from single IP addresses to identify potential DDoS attacks.
- The tutorial emphasizes the importance of understanding cryptocurrency-related activities, as they are increasingly linked to cyber threats and financial motivations.
- Participants are encouraged to use data analysis tools like JQ and DShield-SIEM for effective log analysis and visualization of command execution patterns.
- Strategies for organizations include establishing baselines for normal activity, utilizing automated log analysis tools, and staying updated on threat intelligence to enhance overall cybersecurity defenses.
Analyzing Cybersecurity Anomalies Through Honeypot Activity: A Deep Dive
In a bid to bolster cybersecurity defenses, a newly developed tutorial is offering cybersecurity professionals a comprehensive guide to identifying and analyzing anomalous activities within honeypot data. This initiative aims to equip experts with the skills necessary to detect unusual patterns, particularly in command execution, and to scrutinize potential Distributed Denial of Service (DDoS) indicators. Additionally, it emphasizes the growing importance of understanding cryptocurrency-related activities, which have become increasingly relevant in cybersecurity discussions.
Key Objectives of the Tutorial
Identifying Anomalous Activity
A primary focus of the tutorial is teaching participants how to detect unusual command execution patterns. By concentrating on sessions that exhibit excessive command usage—specifically those exceeding 1,000 commands—cybersecurity professionals can pinpoint potential malicious behavior. This metric serves as a crucial indicator of possible threats, enabling preemptive action.
Analyzing Potential DDoS Indicators
The tutorial also highlights the significance of investigating repeated curl requests directed towards specific websites. Such patterns may suggest DDoS attacks, especially when originating from a single source IP address. Understanding these indicators is vital for taking preemptive measures against potential threats.
Exploring Cryptocurrency-Related Activity
With the increasing intersection between cyber threats and cryptocurrency, the tutorial encourages participants to analyze targeted websites within honeypot activities. By examining these sites, experts can gain insights into the motivations behind observed anomalies, which may relate to financial gain or other illicit purposes.
Utilizing Data Analysis Tools
To facilitate thorough analysis, the tutorial advocates using specialized data analysis tools such as JQ and DShield-SIEM. These tools enable participants to sift through raw logs, visualize command execution patterns, and draw meaningful conclusions across multiple honeypots.
Implications for Cybersecurity
The insights gained from this tutorial are expected to have significant implications for the cybersecurity field. By honing in on anomalous activity and potential threats, cybersecurity professionals will be better equipped to identify and mitigate risks before they escalate into larger issues. The focus on cryptocurrency-related activities is particularly timely, given the ongoing rise in cybercrime associated with digital currencies. Furthermore, the use of advanced data analysis tools will enhance the ability of security teams to interpret complex datasets, ultimately leading to more effective threat detection and response strategies.
Essential Steps for Mastery
-
Understanding the Basics: Establish a solid foundation by familiarizing yourself with key concepts and terminology used throughout the process.
-
Setting Up Your Environment: Prepare your workspace by installing necessary software tools and configuring your system according to specific instructions for your operating system.
-
Implementing Core Techniques: Apply core techniques discussed in the tutorial through hands-on practice to solidify understanding and observe immediate results.
-
Reviewing and Optimizing: Assess your work upon completion of initial tasks, identifying areas for improvement and applying optimization techniques for enhanced performance.
Strategies for Enhanced Cybersecurity Measures
Organizations aiming to enhance their cybersecurity measures should consider several strategies:
-
Establish Baselines: Determine normal network activity baselines to easily identify anomalies that may signal security threats.
-
Utilize Automated Tools: Employ automated tools for log analysis to streamline monitoring processes and pinpoint unusual patterns efficiently.
-
Correlate Data Across Honeypots: Track how threats interact with various systems by correlating data across multiple honeypots for broader attack insights.
-
Conduct Manual Reviews: While automated tools are essential, human oversight is necessary for assessing context and intent in suspicious URLs.
-
Stay Updated on Threat Intelligence: Keep abreast of the latest threats and vulnerabilities to adapt strategies and toolsets effectively against emerging risks.
Common Pitfalls in Honeypot Analysis
When analyzing honeypot activity, particularly unusual command execution like repeated curl requests, users should be aware of common pitfalls:
- Misinterpreting benign activity as malicious
- Overlooking request context
- Failing to correlate data with other security events
Avoiding these mistakes enhances honeypot data analysis and improves overall security posture. Implementing comprehensive monitoring techniques and regularly reviewing logs can help distinguish legitimate traffic from potential attacks.
Tools for Effective Honeypot Management
For effective analysis and management of honeypots like Cowrie:
-
Cowrie: Logs brute-force attacks and captures attacker-issued commands.
-
DShield-SIEM: Integrates with SIEM systems for real-time security incident analysis.
-
JQ: A command-line JSON processor ideal for parsing honeypot-collected data.
-
Google Translate: Useful for interpreting commands from attackers with diverse linguistic backgrounds.
By leveraging these tools, cybersecurity professionals can enhance their honeypot management efforts, gaining deeper insights from collected data and bolstering defenses against cyber threats.