Guidelines for Detecting AS-REP Roasting Attacks
/ 4 min read
Quick take - Organizations are advised to enhance their cybersecurity measures against AS-REP Roasting attacks by systematically monitoring Kerberos-related logs, particularly Event ID 4768, to identify vulnerabilities and potential threats.
Fast Facts
- AS-REP Roasting Threat: Organizations must monitor Kerberos-related logs, particularly Event ID 4768, to detect vulnerabilities and potential AS-REP Roasting attacks.
- Key Log Aspects: Focus on the “Pre-Authentication Type” (value 0 indicates risk), “Ticket Encryption Type” (0x17 is vulnerable), and ensure the “Service Name” is set to krbtgt.
- Log Entry Review: Analyze log entries for accounts with pre-authentication disabled and document originating IP addresses for further investigation.
- Importance of Monitoring: Neglecting log analysis can lead to significant security vulnerabilities, especially in accounts susceptible to AS-REP Roasting.
- Recommended Tools: Utilize tools like Rubeus and Impacket for testing vulnerabilities, along with advanced log analysis software to automate detection of anomalies.
Enhancing Security Measures Against AS-REP Roasting Attacks
In the ever-evolving landscape of cybersecurity, organizations face a myriad of threats that require constant vigilance and proactive measures. Among these threats, AS-REP Roasting attacks have emerged as a significant concern, particularly for systems utilizing Kerberos authentication. Recent guidelines emphasize the importance of systematic monitoring and analysis of specific Kerberos-related logs to identify vulnerabilities, with a particular focus on Event ID 4768.
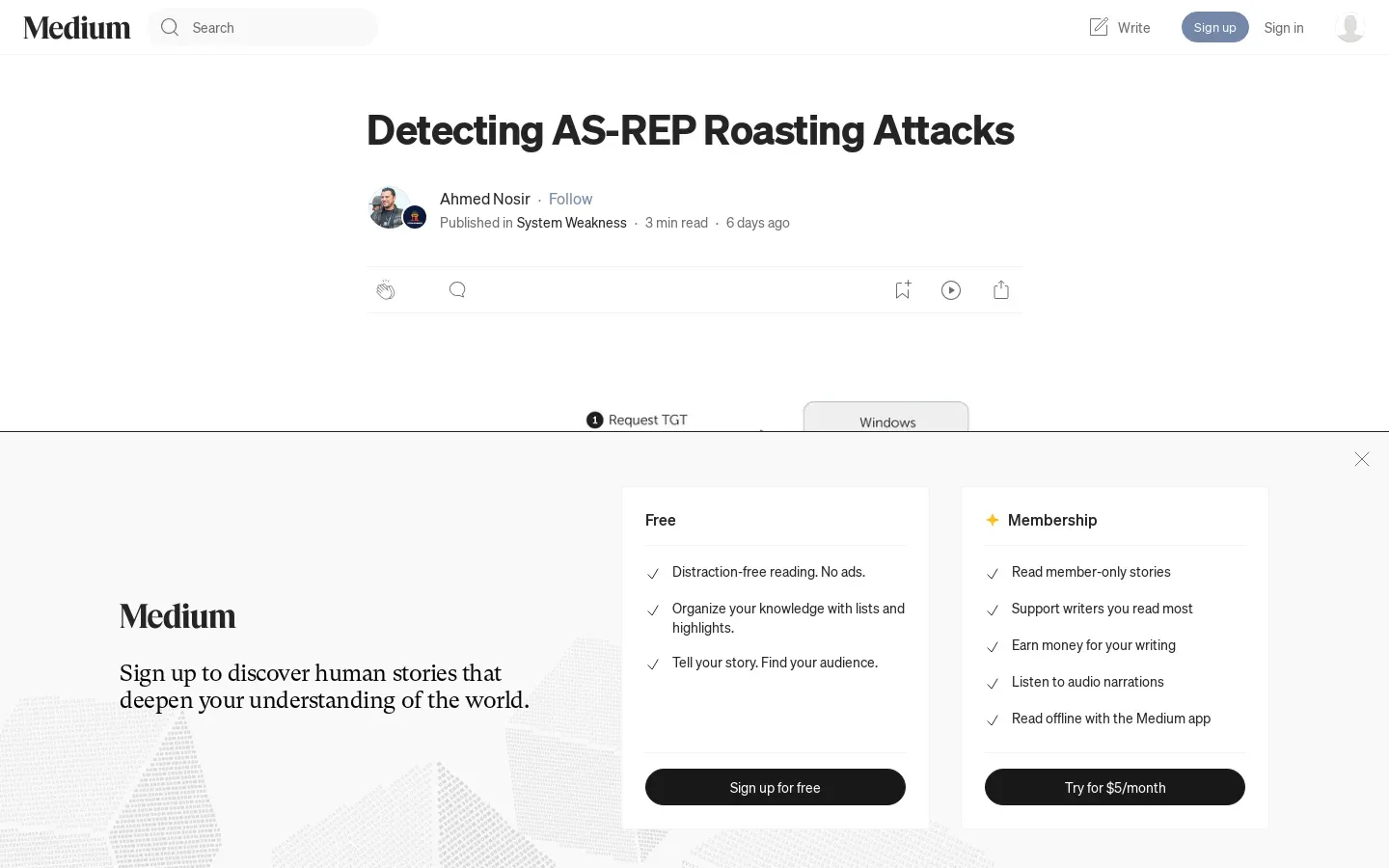
Understanding Event ID 4768
Event ID 4768 is a critical log entry recorded whenever a Kerberos Ticket Granting Ticket (TGT) is issued. This event serves as a primary indicator for identifying potential AS-REP Roasting attempts. Security teams are advised to closely monitor these logs as they can reveal attempts to exploit systems where pre-authentication measures are disabled.
Key Aspects to Monitor
-
Pre-Authentication Type Check: The “Pre-Authentication Type” field within the logs is crucial. A value of 0 indicates that pre-authentication is disabled, significantly increasing the risk of AS-REP Roasting. Attackers can exploit this by requesting TGTs without prior authentication, making it imperative for security teams to flag such instances.
-
Ticket Encryption Type Analysis: The “Ticket Encryption Type” field should be scrutinized for the value 0x17 (RC4-HMAC). This encryption type is commonly targeted by attack tools like Rubeus and Impacket due to its known vulnerabilities. Identifying this encryption type in logs can help pinpoint potential exploitation attempts.
-
Service Name Verification: Ensuring that the “Service Name” field is set to krbtgt is essential. This service is responsible for legitimate Kerberos authentication processes. Any anomalies in this field could indicate malicious activity, warranting further investigation.
-
Log Entry Analysis: A thorough review of log entries for accounts with pre-authentication disabled is necessary. Documenting the originating IP addresses for these requests can provide valuable insights into potential attack vectors and aid in mitigation efforts.
Implications of Inadequate Monitoring
Neglecting to properly analyze these logs can lead to significant security oversights, particularly in accounts with pre-authentication disabled. Ignoring the Pre-Authentication Type could result in missing crucial signs of AS-REP Roasting attempts, leaving networks vulnerable to exploitation. Organizations must prioritize identifying accounts susceptible to these attacks to safeguard their network security effectively.
Moreover, developing practical log analysis skills is vital for cybersecurity personnel. Real-world applications of these concepts empower teams to identify and respond to potential threats efficiently. Understanding the role of legitimate services like krbtgt in Kerberos authentication is crucial for differentiating between benign and malicious activities within system logs.
Recommended Tools and Resources
To bolster defenses against AS-REP Roasting, several tools and resources are recommended:
-
Rubeus: This tool allows for manipulation and abuse testing of Kerberos tickets, helping identify vulnerabilities within Kerberos implementations.
-
Impacket: A collection of Python classes designed for working with network protocols, Impacket assists in crafting and sending Kerberos authentication requests.
-
Log Analysis Software: Advanced log analysis tools can automate the detection of unusual patterns or anomalies in Event ID 4768 logs, enhancing monitoring efficiency.
By implementing these monitoring practices and utilizing the recommended tools, organizations can strengthen their defenses against AS-REP Roasting attacks and enhance their overall cybersecurity posture.