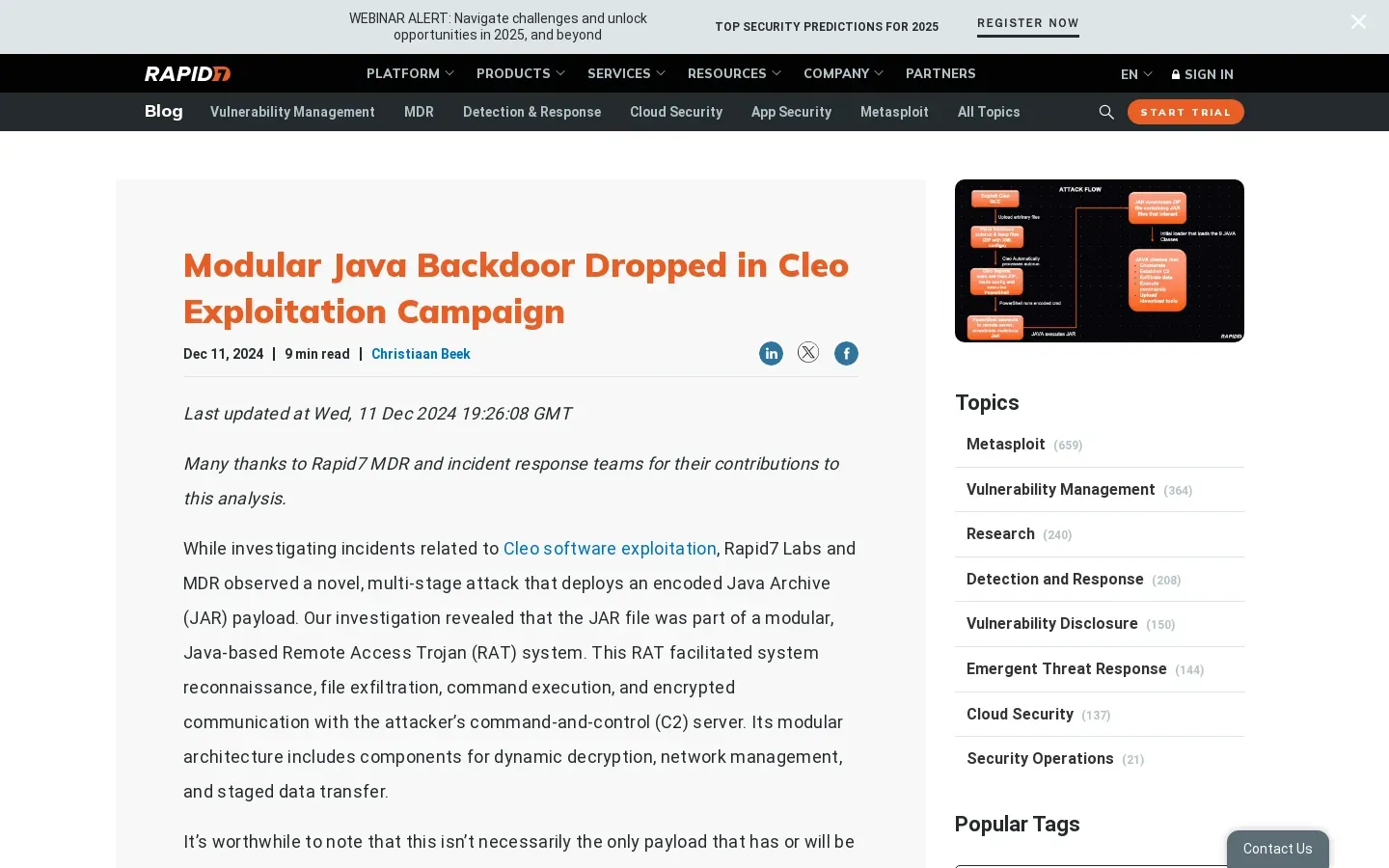
Cleo Software Exploitation Highlights Need for Cybersecurity Improvements
/ 4 min read
Quick take - Recent research on the exploitation of Cleo software has identified critical vulnerabilities and sophisticated attack methods, emphasizing the need for organizations to enhance their cybersecurity measures and adopt proactive defense strategies.
Fast Facts
- Recent research reveals critical vulnerabilities in Cleo software, highlighting the need for improved cybersecurity measures against sophisticated attacks.
- Key findings include incident analysis, vulnerability mapping, and dynamic behavior analysis of Remote Access Trojans (RATs) used in exploits.
- The study emphasizes the importance of enhanced detection and response strategies, proactive zero-day vulnerability management, and securing supply chains.
- Tools and techniques discussed include JAR payloads, PowerShell scripting, XOR encryption, and XML configuration vulnerabilities.
- Future recommendations focus on gamified training modules to improve employee awareness and preparedness against cyber threats.
Unveiling the Exploitation of Cleo Software: A Call for Enhanced Cybersecurity
Recent research into the exploitation of Cleo software has brought to light critical vulnerabilities and sophisticated attack vectors, emphasizing the urgent need for improved cybersecurity measures. This comprehensive analysis not only identifies key threats associated with Cleo software but also delves into the methodologies employed by attackers, highlighting the necessity for organizations to fortify their defenses against such advanced threats.
Incident Analysis and Threat Identification
The investigation begins with a detailed examination of incidents involving Cleo software. Researchers have identified patterns and specific threat actors responsible for exploiting its vulnerabilities. These findings underscore the importance of understanding the tactics, techniques, and procedures (TTPs) used by cybercriminals to infiltrate systems. By recognizing these patterns, organizations can better anticipate potential threats and implement preemptive measures.
Code Examination and Vulnerability Mapping
A critical component of the research involved a meticulous code examination to map out vulnerabilities within Cleo software. Researchers pinpointed several critical weaknesses that could be exploited by attackers, providing a clear roadmap for potential intrusions. This vulnerability mapping is essential for developers and security professionals aiming to patch these weaknesses before they can be leveraged in attacks.
Dynamic Behavior Analysis of RAT
The study also conducted a dynamic behavior analysis of the Remote Access Trojan (RAT) used in these exploits. This analysis revealed the methods employed by attackers to infiltrate and manipulate systems, offering insights into how RATs are deployed and controlled remotely. Understanding these dynamics is crucial for developing effective countermeasures that can detect and neutralize such threats in real-time.
Indicators of Compromise and Threat Intelligence Sharing
Identifying Indicators of Compromise (IOCs) has been a pivotal aspect of this research. By sharing these IOCs across organizations, there is an opportunity to enhance collective defense strategies. Threat intelligence sharing allows organizations to stay informed about emerging threats and adapt their security measures accordingly, fostering a more resilient cybersecurity ecosystem.
Supporting Details: Strengthening Security Measures
The findings emphasize several areas where robust security measures are paramount:
-
Enhanced Detection and Response Strategies: Organizations are urged to adopt advanced detection and response systems capable of swiftly identifying and mitigating threats.
-
Zero-Day Vulnerability Management: Proactive management of zero-day vulnerabilities is critical, ensuring timely patches and updates to close potential entry points for attackers.
-
Modular Malware Defense: A modular approach to malware defense is recommended, allowing for flexible and adaptive security measures tailored to specific threats.
-
Supply Chain Security Considerations: Securing supply chains is vital, as vulnerabilities in third-party software can serve as gateways for attacks.
Tools and Techniques Explored
The research explored various tools, frameworks, and techniques that can be employed to defend against Cleo software exploitation:
-
Java Archive (JAR) Payload: Analysis focused on how JAR payloads are utilized in attacks to deliver malicious content.
-
PowerShell Scripting: The role of PowerShell scripts in executing commands and exploiting vulnerabilities was examined.
-
XOR Encryption: Techniques used for obfuscating malicious code to evade detection were analyzed.
-
Cleo Integration Suite Configuration (XML): Examination of XML configurations that could lead to security gaps was conducted.
Future Directions: Building a Culture of Security Awareness
As organizations strive to enhance their security posture, the research suggests focusing on developing gamified training modules. These programs simulate real-world attack scenarios, providing employees with opportunities to practice identifying and responding to potential threats in a controlled environment. Such initiatives foster a culture of security awareness and preparedness, equipping teams with the skills needed to navigate an increasingly complex threat landscape.
In light of these findings, organizations must prioritize strengthening their cybersecurity frameworks. By implementing the insights gained from this research, they can better protect themselves against sophisticated cyber threats targeting Cleo software.