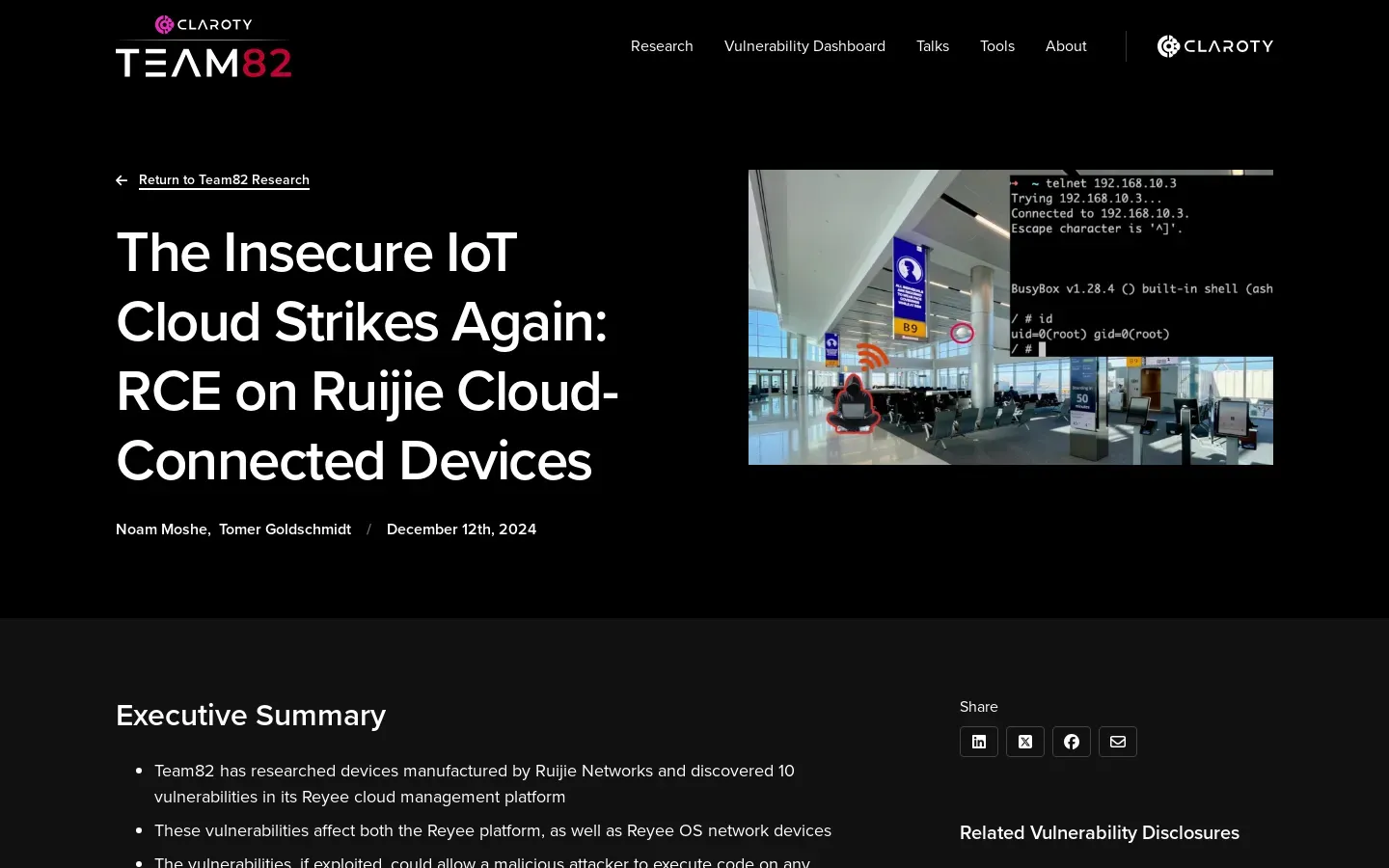
Critical Vulnerabilities Found in Ruijie Cloud Management Platform
/ 4 min read
Quick take - Team82’s recent study has identified critical vulnerabilities in Ruijie Networks’ Reyee cloud management platform, highlighting the need for improved cybersecurity measures for Internet of Things (IoT) devices and their management systems.
Fast Facts
- Team82’s study reveals critical vulnerabilities in Ruijie Networks’ Reyee cloud management platform, highlighting security concerns for IoT devices.
- Key research methods included analyzing the attack surface, firmware decryption, and exploiting MQTT communication to identify weaknesses.
- Findings emphasize the need for improved cloud security protocols, vulnerability disclosure processes, and awareness of serial number security risks.
- The research utilized tools like QEMU, Wireshark, and Python scripting to uncover vulnerabilities, though it noted limitations in the scope of devices tested.
- Recommendations include developing enhanced security protocols, automated vulnerability detection tools, and public awareness programs to strengthen IoT security.
Team82 Uncovers Critical Vulnerabilities in Ruijie Networks’ Reyee Cloud Management Platform
In a significant development for the cybersecurity community, Team82 has identified critical vulnerabilities within Ruijie Networks’ Reyee cloud management platform. This discovery raises urgent questions about the security of Internet of Things (IoT) devices and their associated management systems, underscoring the pressing need for enhanced cybersecurity measures as reliance on cloud services continues to grow.
Unveiling the Attack Surface
The investigation by Team82 was comprehensive, focusing on dissecting the security posture of the Reyee platform through a multifaceted approach. A primary objective was to understand the attack surface by identifying potential entry points and weaknesses within the cloud management system. This involved a detailed analysis of the firmware to uncover hidden vulnerabilities and security flaws that could be exploited by malicious actors.
Exploiting MQTT Communication
A key component of the research was examining the MQTT protocol, which is commonly used for IoT communications. The team scrutinized how attackers could manipulate data exchanges via this protocol, leading to the development of a practical exploit known as the “Open Sesame Attack.” This exploit demonstrated significant security gaps within the platform, highlighting vulnerabilities that could be leveraged to compromise IoT devices managed through Reyee.
Implications for Cloud Security
The findings from Team82’s research have far-reaching implications for the cybersecurity landscape. One major takeaway is the increased focus needed on cloud security for IoT devices. As these devices become more integrated into daily operations, securing their cloud infrastructures becomes paramount. The study also emphasizes the importance of robust vulnerability disclosure and response protocols to address security issues promptly.
Serial Number Security Concerns
Another critical aspect highlighted by the research is the security risks associated with serial number exposure. The study suggests that better protective measures are necessary to safeguard these identifiers from being exploited by attackers. Additionally, it illustrates how targeted attack strategies can be developed by exploiting specific weaknesses in cloud management systems.
Research Strengths and Limitations
Team82’s research stands out for its comprehensive approach and relevance to contemporary cybersecurity challenges. However, there are limitations, particularly regarding the scope of devices tested and potential undiscovered vulnerabilities in other IoT ecosystems. Future investigations could expand on these findings to encompass a broader range of IoT devices, providing a more holistic view of potential threats.
Tools and Techniques Utilized
The research employed various tools and frameworks to uncover vulnerabilities:
- QEMU: Used for emulating hardware and enabling firmware analysis.
- Wireshark: A network protocol analyzer that facilitated examination of MQTT communication.
- MQTT Protocol: A lightweight messaging protocol pivotal for IoT devices, whose vulnerabilities were scrutinized.
- Python Scripting: Utilized to automate processes and streamline analysis.
Recommendations for Future Actions
To mitigate identified risks and enhance IoT device security, several actionable initiatives are recommended:
- Enhanced Security Protocols: Develop robust security measures tailored specifically for IoT environments.
- Automated Vulnerability Detection Tools: Implement tools capable of continuously scanning for vulnerabilities in real-time.
- Incident Response Frameworks: Establish protocols to respond swiftly to identified threats.
- Public Awareness Programs: Educate stakeholders about potential risks and best practices to safeguard their IoT infrastructures.
By addressing these areas, stakeholders can contribute to a more resilient IoT ecosystem, significantly reducing exploitation risks and improving overall security posture against evolving threats.