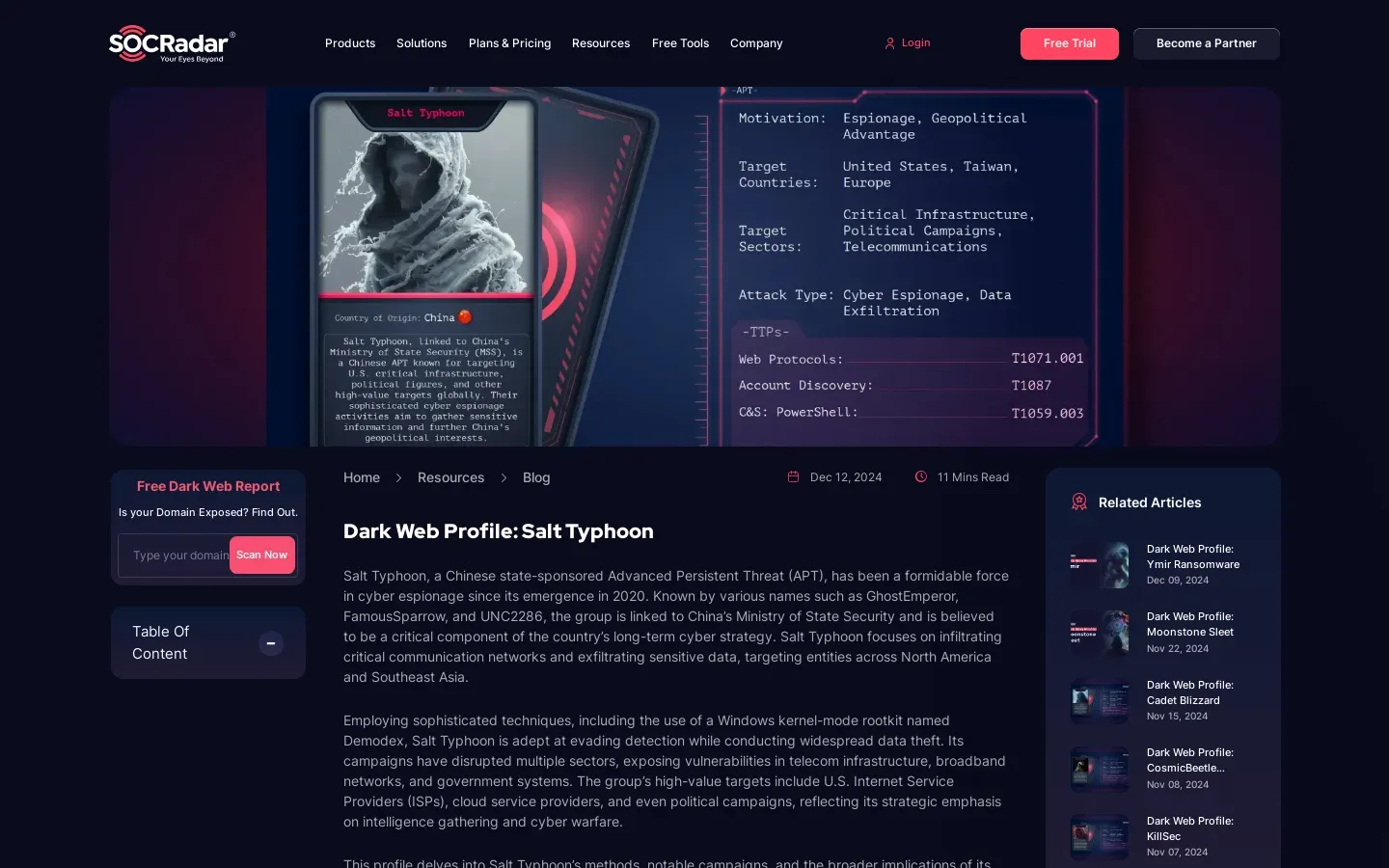
Emergence of Salt Typhoon as a Cyber Threat
/ 4 min read
Quick take - The emergence of Salt Typhoon as a state-sponsored cyber threat has prompted a comprehensive analysis of its operational tactics and implications for cybersecurity, highlighting the need for enhanced threat intelligence sharing, the adoption of Zero Trust architecture, and investment in advanced detection tools.
Fast Facts
- Emergence of Salt Typhoon: Identified as a significant state-sponsored cyber threat, prompting a detailed analysis of its tactics and implications for cybersecurity.
- Research Focus Areas: Key objectives include profiling Salt Typhoon, analyzing its attack campaigns, mapping its tactics, and recommending defense strategies.
- Key Findings: Emphasizes the need for enhanced threat intelligence sharing, adoption of Zero Trust architecture, and investment in advanced detection and response tools.
- Strengths and Limitations: Provides a comprehensive understanding of state-sponsored threats but highlights the need for continual updates and real-world testing of defense strategies.
- Future Exploration: Suggests avenues for further research, including advanced threat detection systems, public-private sector collaboration, and cybersecurity training programs.
The Emergence of Salt Typhoon: A New Cyber Threat on the Horizon
In a rapidly evolving cyber threat landscape, the emergence of Salt Typhoon as a formidable state-sponsored actor has captured the attention of cybersecurity experts worldwide. Recent research delves into the operational tactics and implications of this new threat, aiming to bolster defense strategies and foster collaboration within the cybersecurity community.
Understanding Salt Typhoon: Profiling a State-Sponsored Actor
The research begins by developing a comprehensive profile of Salt Typhoon, focusing on its origins, motivations, and operational patterns. As a state-sponsored entity, Salt Typhoon is believed to operate with specific geopolitical objectives, targeting critical infrastructure and sensitive data. Intelligence gathering efforts have been pivotal in piecing together the group’s modus operandi, providing valuable insights into its strategic goals.
Analyzing Attack Campaigns: Unveiling Methods and Impacts
Salt Typhoon’s attack campaigns are characterized by their precision and sophistication. The research identifies several high-profile targets across various sectors, including government agencies, financial institutions, and technology firms. By dissecting these campaigns, experts have uncovered a range of methods employed by Salt Typhoon, from spear-phishing attacks to exploiting zero-day vulnerabilities. The impacts of these attacks are far-reaching, often resulting in significant data breaches and operational disruptions.
Mapping Tactics, Techniques, and Procedures (TTPs)
A critical component of the research involves mapping the specific Tactics, Techniques, and Procedures (TTPs) used by Salt Typhoon. This mapping enhances predictive capabilities, allowing organizations to anticipate potential threats and adapt their defenses accordingly. The documented TTPs reveal a reliance on advanced malware, lateral movement within networks, and sophisticated evasion techniques designed to bypass traditional security measures.
Recommendations for Defense Strategies
In response to the threat posed by Salt Typhoon, the research offers actionable strategies for organizations to strengthen their defenses. Key recommendations include:
-
Enhanced Threat Intelligence Sharing: Encouraging organizations to collaborate more closely and share intelligence to create a unified front against emerging threats.
-
Adoption of Zero Trust Architecture: Emphasizing a security model that assumes threats could be internal or external, enforcing strict access controls throughout the network.
-
Investment in Advanced Detection and Response Tools: Highlighting the need for sophisticated tools capable of detecting and responding to threats in real-time.
Strengths and Limitations of the Research
The research provides an in-depth analysis of Salt Typhoon’s operations, offering a solid foundation for understanding state-sponsored cyber threats’ complexities. However, it also acknowledges limitations such as the dynamic nature of cyber threats necessitating continual updates to threat profiles and TTPs. Additionally, the effectiveness of recommended defense strategies requires real-world testing and adaptation.
Tools and Techniques: A Closer Look
Several tools and frameworks are discussed as critical to understanding Salt Typhoon’s operations:
-
Threat Intelligence Platforms: These platforms aggregate and analyze threat data from various sources to provide actionable insights.
-
Behavioral Analysis Tools: Used to monitor network traffic for anomalies that may indicate a breach.
-
Incident Response Frameworks: Guidelines ensuring a coordinated approach when responding to cyber incidents.
Future Exploration Areas
The research points towards several avenues for further exploration:
-
Development of Advanced Threat Detection Systems: Innovating detection technologies leveraging AI and machine learning.
-
Enhanced Collaboration Between Public and Private Sectors: Creating partnerships to strengthen defenses and share critical threat intelligence.
-
Focus on Zero Trust Architecture Implementation: Further research into best practices for implementing Zero Trust principles across varied organizational structures.
-
Cybersecurity Awareness and Training Programs: Developing comprehensive training programs to enhance employee awareness against cyber threats.
As Salt Typhoon continues to evolve as a cyber threat, organizations must adopt proactive measures to safeguard their infrastructures. The insights gained from this research not only inform current defense strategies but also pave the way for future advancements in cybersecurity practices. By fostering collaboration and innovation within the cybersecurity community, stakeholders can better prepare for the challenges posed by increasingly sophisticated adversaries like Salt Typhoon.