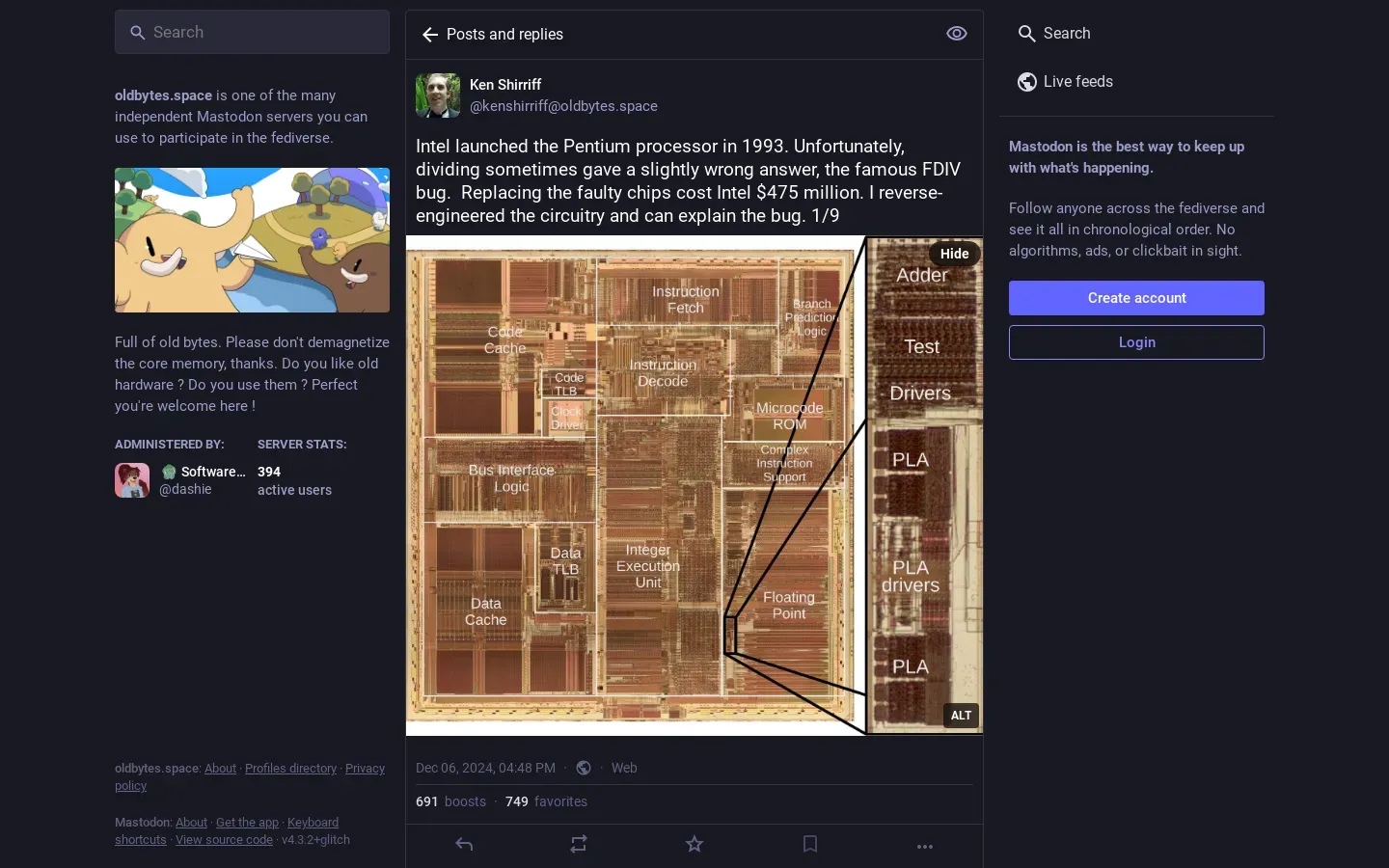
Intel Pentium Processor Defect Raises Security Concerns
/ 3 min read
Quick take - A defect in Intel’s Pentium processors has raised security concerns for a video game developer, prompting the company to expand its replacement policy for affected CPUs while highlighting the potential risks of account takeovers and data breaches associated with the vulnerabilities.
Fast Facts
- A defect in Intel’s Pentium processors has raised significant security concerns for a major video game developer, prompting Intel to expand its replacement policy for affected CPUs.
- The vulnerabilities linked to the defective processors could lead to unauthorized account access, phishing attacks, and potential data breaches, threatening user privacy and organizational integrity.
- Organizations face risks of Denial of Service (DoS) attacks, which could disrupt services and result in system downtime.
- Reputational damage and loss of customer trust may have financial repercussions for companies affected by these vulnerabilities.
- A positive note includes Dell’s prompt response in replacing defective processors, highlighting the importance of proactive customer service during technical crises.
Intel Pentium Defect Sparks Security Concerns for Video Game Developer
In a recent revelation, a defect in Intel’s Pentium processors has emerged as a critical issue for computers used by a leading video game developer. Initially, Intel downplayed the severity of the defect, assuring users that it posed no significant threat. However, as more information surfaced, the company revised its stance, first offering CPU replacements only to identified affected customers. Eventually, Intel expanded this offer to all customers with faulty processors.
Security Implications and Vulnerabilities
The implications of this defect extend beyond mere hardware malfunctions. The vulnerabilities associated with the defective Pentiums raise serious security concerns, particularly regarding account takeovers. These vulnerabilities could allow unauthorized access to user accounts, enabling attackers to impersonate legitimate users and engage in malicious activities. Furthermore, exploiting these vulnerabilities could facilitate phishing attacks, making it easier for attackers to craft convincing messages and gain access to sensitive information.
The potential fallout from these vulnerabilities is significant. Organizations could face data breaches that compromise sensitive information and threaten both user privacy and organizational integrity. Additionally, there is an increased risk of Denial of Service (DoS) attacks. Exploitable vulnerabilities may allow attackers to disrupt services, leading to downtime for affected systems.
Broader Impact on Organizations
The reputational damage for organizations impacted by these vulnerabilities cannot be understated. Loss of customer trust may follow, resulting in financial repercussions that could affect the company’s bottom line. In an industry where reputation is paramount, such incidents can have long-lasting effects on customer relationships and market position.
Positive Responses Amidst Challenges
Despite the challenges posed by the defect, some companies have demonstrated exemplary customer service. For instance, Dell promptly dispatched a technician to replace defective Pentium processors at their office in Austin. This proactive approach underscores the importance of responsive and responsible actions during technical crises.
Vigilance and Preparedness: Key Takeaways
As the situation continues to unfold, it remains crucial for affected organizations and users to stay vigilant against potential security threats arising from these vulnerabilities. While specific technical details or remediation steps have not been disclosed, the overarching message emphasizes the need for heightened awareness and preparedness in addressing hardware-related issues.
Organizations should consider conducting thorough security audits and implementing robust monitoring systems to detect any unusual activity promptly. Additionally, maintaining open communication channels with hardware vendors can ensure timely updates and support in mitigating potential risks associated with such defects.