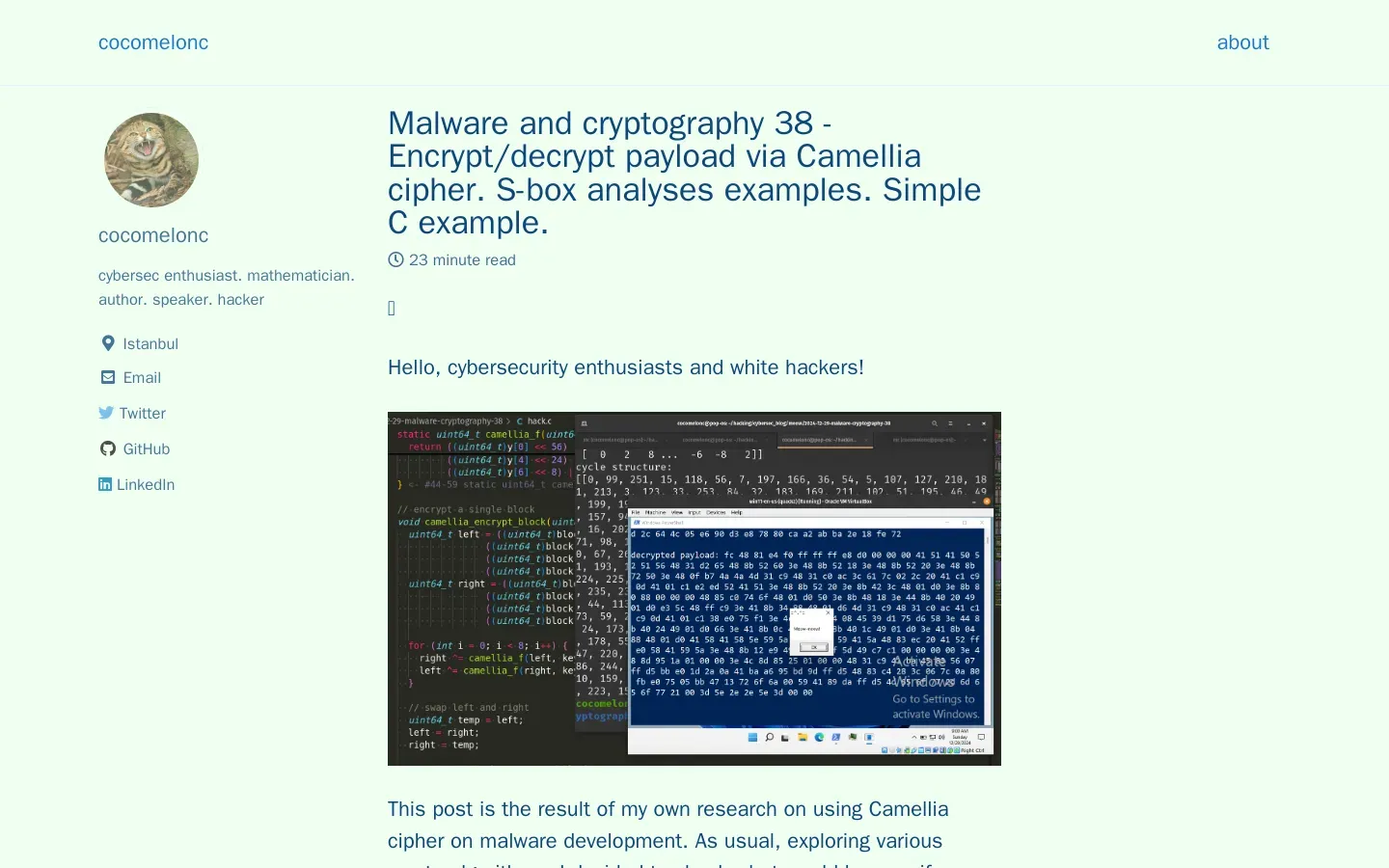
Camellia Cipher: Structure, Implementation, and Best Practices
/ 4 min read
Quick take - The article provides an overview of the Camellia cipher, a symmetric key block cipher known for its robust security and efficient performance, detailing its structure, implementation best practices, common pitfalls, and available tools for effective cryptanalysis.
Fast Facts
- The Camellia cipher, developed in 2000 by Mitsubishi Electric and NTT Corporation, is a symmetric key block cipher known for its robust security and efficient performance, utilizing a Feistel network structure.
- It employs four S-boxes to enhance non-linearity and resistance to cryptographic attacks, with a critical rotate left macro for achieving diffusion during encryption rounds.
- Best practices for implementation include understanding the Feistel network, utilizing all S-boxes, ensuring correct padding, and conducting rigorous cryptanalysis to evaluate security.
- Common pitfalls to avoid include misunderstanding the cipher’s structure, neglecting proper encryption processes, and inadequate cryptanalysis of custom implementations.
- Recommended tools for implementation include MessageBox Payload for demonstration, EnumDesktopsA for practical applications, Shannon Entropy Calculation for randomness analysis, and essential S-boxes and constants for security.
Understanding the Camellia Cipher: A Deep Dive into its Structure and Implementation
In the ever-evolving landscape of cryptography, the Camellia cipher has emerged as a noteworthy player. Developed in 2000 by Mitsubishi Electric and NTT Corporation, this symmetric key block cipher is recognized for its robust security features and efficient performance. As a Feistel network-based cipher, Camellia’s structured approach to encryption and decryption has piqued the interest of researchers and developers alike.
Key Features and Structure
At the core of the Camellia cipher is its utilization of a Feistel network, a method that processes data in blocks to enhance both encryption and decryption processes. This structure is complemented by four S-boxes, which are pivotal in ensuring non-linearity and resistance to cryptographic attacks. These S-boxes, along with specific constants, are designed to withstand rigorous cryptanalysis.
A critical component of Camellia’s encryption process is the rotate left macro. This operation performs circular left shift operations, crucial for achieving diffusion during multiple encryption rounds. Such diffusion ensures that minor changes in input result in significant alterations in output, bolstering the cipher’s security.
Implementation Best Practices
Implementing the Camellia cipher effectively requires adherence to several best practices:
-
Thorough Understanding of Structure: Developers must familiarize themselves with the Feistel network structure to understand how data is processed.
-
Utilization of All S-boxes: Incorporating all four S-boxes according to the Camellia standard is vital for enhancing security.
-
Correct Padding Implementation: Proper handling of padding for the last block, such as using the NOP byte, is crucial for maintaining data integrity during encryption.
-
Rigorous Cryptanalysis: Conducting analyses like differential uniformity, linear approximation, and evaluating the avalanche effect is necessary to assess resilience against potential attacks.
Common Mistakes to Avoid
While implementing the Camellia cipher, certain pitfalls must be avoided:
- A lack of understanding of the cipher’s foundational structure can lead to ineffective implementations.
- Neglecting proper execution of encryption and decryption processes, including S-box usage and Feistel network operations.
- Overlooking essential cryptanalysis techniques needed to evaluate the cipher’s security.
- Inadequate analysis of custom ciphers due to insufficient experience in modifying scripts for cryptographic evaluation.
Tools and Resources for Implementation
Several tools and resources can aid in implementing the Camellia cipher:
-
MessageBox Payload: This straightforward payload helps demonstrate encryption and decryption processes, verifying implementation correctness.
-
EnumDesktopsA: A function that allows payloads to run on a victim’s machine, showcasing practical applications of Camellia in malware scenarios.
-
Shannon Entropy Calculation: Analyzing payload randomness plays a critical role in assessing encryption strength.
-
S-boxes and Constants: Essential components for ensuring non-linearity and resistance to attacks, as highlighted in tutorials.
The Camellia cipher stands out as a strong symmetric key block cipher, offering an effective blend of security and performance. By understanding its structure and adhering to best practices during implementation, developers can leverage its capabilities effectively. As cryptography continues to evolve, ongoing research and analysis of ciphers like Camellia will remain crucial in safeguarding digital information.