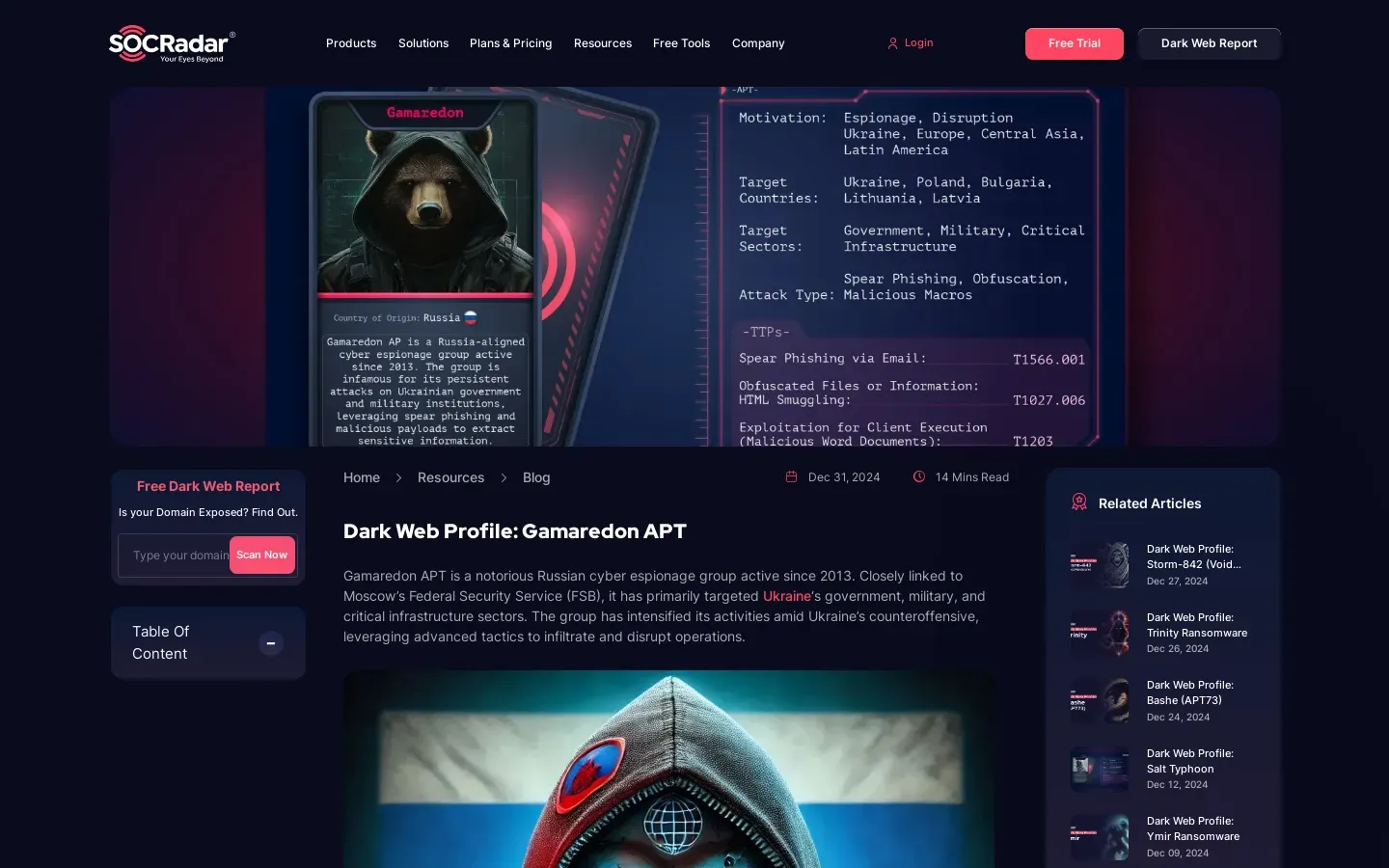
Gamaredon APT: Cybersecurity Threat Analysis and Insights
/ 4 min read
Quick take - Recent research into the Gamaredon Group has provided valuable insights into their tactics and methodologies, highlighting the need for enhanced cybersecurity measures and ongoing investigation to counteract their persistent threats.
Fast Facts
- Recent research on the Gamaredon Group reveals their advanced tactics, techniques, and procedures (TTPs), emphasizing the need for improved detection and response mechanisms.
- The study identified the use of obfuscated PowerShell scripts and Virtual Network Computing (VNC) tools for staging attacks and maintaining control over compromised systems.
- Findings highlight the importance of automated threat hunting tools to continuously monitor for indicators of compromise (IOCs) associated with the Gamaredon Group.
- The research provides actionable insights for organizations, enhancing user awareness and training to better recognize and respond to cyber threats.
- Future directions include exploring AI applications in threat hunting and the necessity for organizations to stay updated on evolving cybersecurity regulations.
In an age where cyber threats loom larger than ever, the push for robust cybersecurity measures has never been more critical. The Gamaredon Group, a notorious cybercriminal organization, has emerged as a formidable player in this landscape, utilizing sophisticated tactics to breach defenses and compromise sensitive data. As organizations scramble to fortify their shields against such adversaries, understanding the group’s Tactics, Techniques, and Procedures (TTPs) is paramount. Recent research sheds light on enhanced detection and response mechanisms, revealing both the strengths of current defenses and areas ripe for improvement.
One of the standout discoveries is the use of PowerShell scripts—specifically obfuscated ones—for staging malicious activities. This technique underscores the need for advanced malware behavior analysis that can dissect these scripts, allowing security experts to identify specific indicators of compromise (IOCs) effectively. By mapping out the Gamaredon Group’s TTPs, researchers can craft tailored signatures for detection that significantly bolster the security posture of potential targets. This proactive approach not only mitigates risks but also enhances overall incident response capabilities.
Equally alarming is the group’s employment of Virtual Network Computing (VNC) tools, such as UltraVNC, to remotely control compromised hosts. This highlights a critical area for infrastructure hardening and monitoring, as organizations must invest in systems that can detect unauthorized remote access attempts. Enhanced monitoring tools should be designed to flag anomalies in network traffic patterns or unusual file access behaviors indicative of VNC usage. By integrating these insights into an organization’s cybersecurity framework, businesses can create a more resilient environment against such invasions.
The implications of these findings extend beyond immediate threat detection; they pave the way for innovative applications in real-world scenarios. For instance, the development of automated threat hunting tools could revolutionize how organizations track Gamaredon Group’s activities. These tools could continuously scan for IOCs associated with their operations—be it specific file patterns or registry changes—effectively preempting potential breaches before they escalate into full-blown incidents.
Yet, while technological advancements are crucial, they must be coupled with a focus on user awareness training. Employees often represent the first line of defense against cyber threats; thus, fostering a culture of vigilance through ongoing education about recognizing phishing attempts and other social engineering tactics is essential. By enhancing user awareness, organizations can significantly reduce their vulnerability to attacks that exploit human error.
Despite these advancements, challenges remain. The research points out several limitations in current methodologies and indicates areas for further investigation. Future directions could include leveraging artificial intelligence to enhance threat hunting capabilities. Machine learning algorithms could analyze vast datasets generated from network activities to identify patterns that human analysts might miss, thereby enabling organizations to stay one step ahead of adversaries like the Gamaredon Group.
As we look forward, the evolving landscape of cybersecurity will inevitably shape our strategies and technologies. The Gamaredon Group serves as a reminder of the persistent threats lurking in the shadows of our digital world. Nevertheless, by harnessing advanced detection techniques, automating monitoring processes, and cultivating informed user bases, organizations can forge a path toward a more secure future that not only withstands today’s challenges but anticipates tomorrow’s threats. The race against cybercrime is relentless, but with each discovery comes an opportunity to fortify defenses and safeguard our digital future.