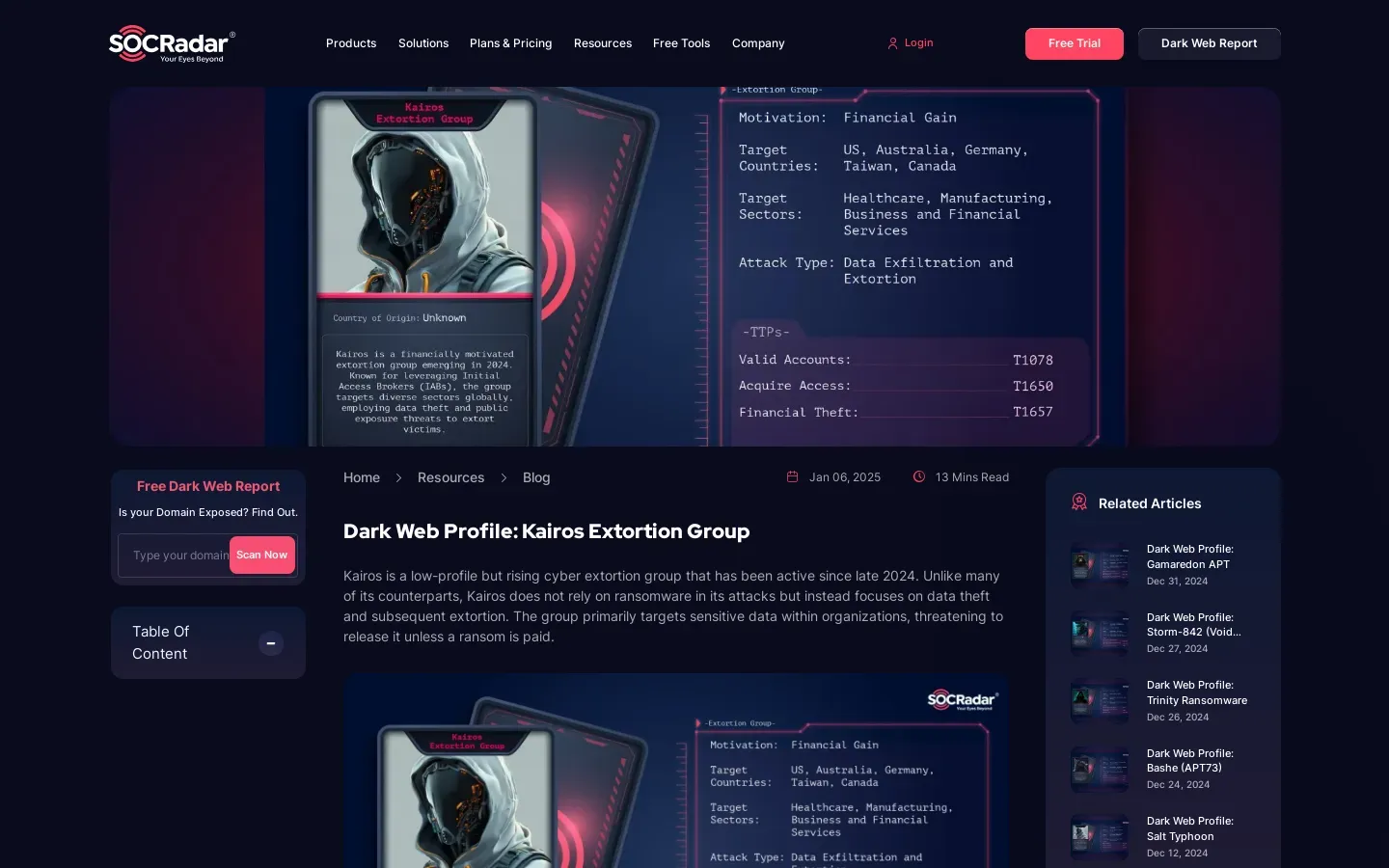
Kairos Extortion Group Targets Critical Sectors in Cybercrime
/ 4 min read
Quick take - Recent research into the Kairos Extortion Group reveals their operational tactics in cybercrime, particularly targeting sensitive sectors, and offers strategies for enhancing cybersecurity defenses against their activities.
Fast Facts
- The Kairos Extortion Group targets sensitive sectors like healthcare, finance, and education, using Initial Access Brokers (IABs) for infiltration and data exfiltration to extort victims.
- Their strategy includes threatening public exposure of stolen data and utilizing Data-Leak Sites (DLS) to increase pressure on organizations.
- The research emphasizes the need for sector-specific cybersecurity frameworks and investment in initial access defense mechanisms to prevent IAB infiltration.
- Recommendations include enhancing data protection measures and developing advanced threat intelligence platforms for monitoring extortion group activities.
- Future research should focus on tailored threat intelligence systems and incident response plans to effectively counter evolving cyber extortion tactics.
In an era where digital infrastructure underpins nearly every aspect of our lives, the rise of cyber extortion groups like the Kairos Extortion Group has alarmed both businesses and individuals alike. These nefarious entities have honed their tactics, targeting vital sectors such as healthcare, finance, and education. As they exploit vulnerabilities within these industries, the need for a robust cybersecurity framework becomes increasingly pressing. A recent study on Kairos sheds light on its operational methodology and presents several strategies to counteract its malevolent influence.
The initial access broker (IAB) model stands out as a critical element in Kairos’s operations. By leveraging IABs, the group gains entry into secure systems, often selling this access to other cybercriminals. This method not only broadens their reach but also complicates the landscape for cybersecurity professionals who must identify and mitigate threats from multiple fronts. Given this dynamic, organizations must prioritize investment in initial access defense mechanisms that fortify their perimeters against unauthorized entry.
As Kairos intensifies its focus on data exfiltration, it threatens public exposure of sensitive information, compelling victims to comply with ransom demands. The psychological toll on organizations is substantial, particularly for those in sectors where data privacy is paramount. In response, businesses must adopt a more vigilant stance towards data protection and privacy—implementing stringent policies that safeguard sensitive information from falling into the hands of malicious actors. This proactive approach not only shields data but also reinforces trust with clients and stakeholders.
The research highlights the importance of sector-specific cybersecurity frameworks tailored to the unique challenges faced by industries targeted by extortion groups. For instance, healthcare organizations deal with life-critical data that cannot be compromised without dire consequences. Thus, developing incident response plans specific to extortion scenarios is essential. These plans should include clear protocols for communication, containment strategies, and recovery processes that mitigate damage while safeguarding patient confidentiality.
In tandem with these defensive strategies, there’s a pressing need for enhanced focus on data-leak sites (DLS)—online platforms where stolen data is posted to pressure victims into paying ransoms. Monitoring these sites can provide valuable intelligence regarding emerging threat vectors and victim trends. Cybersecurity firms should invest in technologies capable of conducting real-time dark web monitoring to detect potential breaches before they escalate.
A forward-looking perspective reveals a growing trend toward Zero Trust Architecture, which emphasizes never trusting any entity by default—whether inside or outside an organization’s network perimeter. Implementing this philosophy requires a cultural shift within organizations, fostering an environment where security is everyone’s responsibility. It compels companies to verify every request as if it originates from an untrusted source.
As we consider future implications in combating groups like Kairos, there is a pivotal opportunity for research to focus on developing advanced threat intelligence platforms that not only monitor but also analyze the activities of such extortion groups comprehensively. These platforms should integrate seamlessly with existing cybersecurity tools through APIs, facilitating automated responses to detected threats and enhancing overall security posture.
In summary, while the threat posed by cyber extortion groups like Kairos is formidable, proactive measures—including strengthening initial access defenses, emphasizing data protection tailored to sector-specific needs, and leveraging dark web intelligence—can mitigate risks significantly. The evolution of cybercrime models demands an equally adaptive response from organizations worldwide as they navigate an increasingly perilous digital landscape. Embracing these changes will not only bolster defenses but also pave the way for a more resilient future against cyber threats.