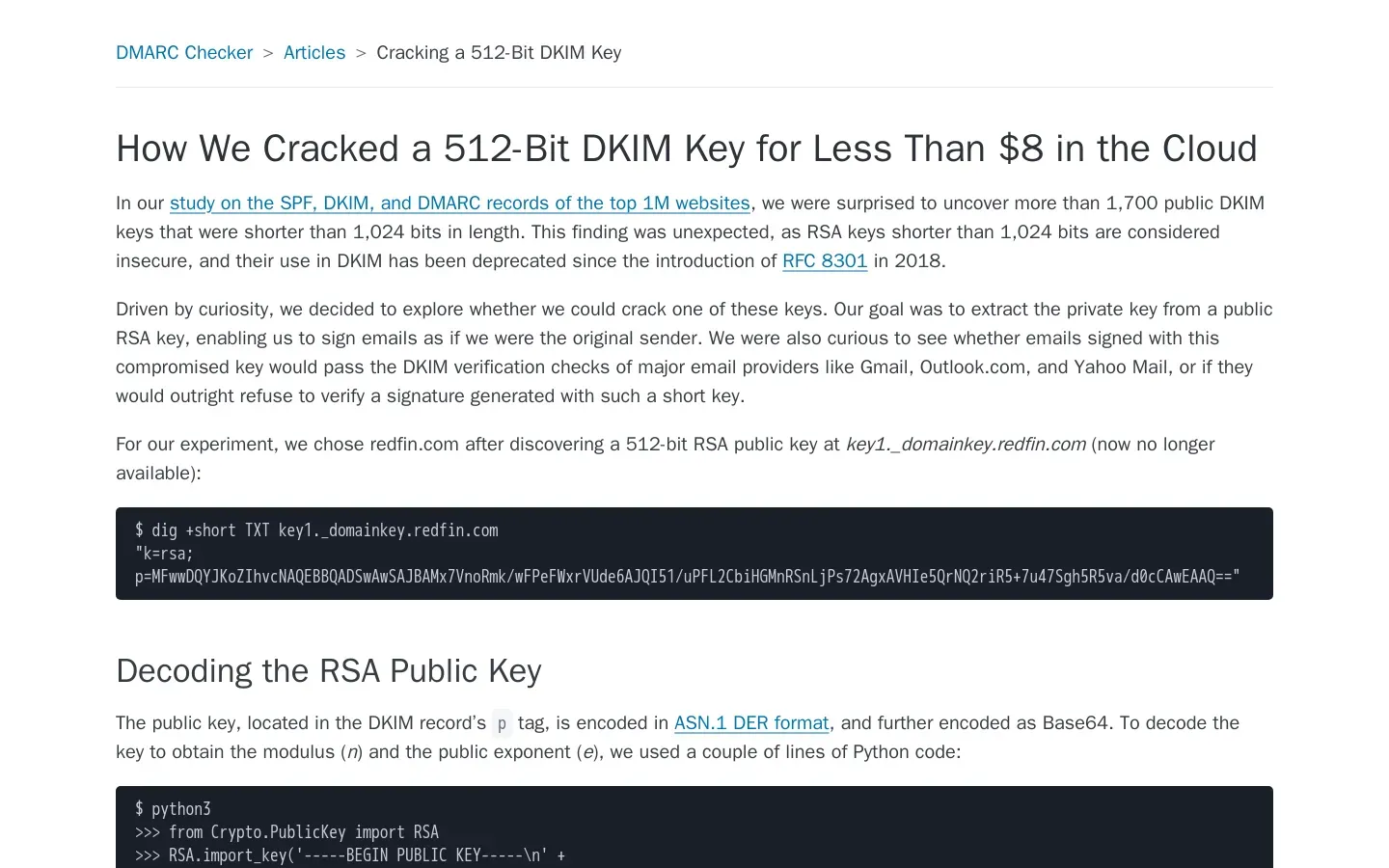
Research Reveals Vulnerabilities in 512-Bit DKIM Keys
/ 4 min read
Quick take - Recent research has identified critical vulnerabilities in DomainKeys Identified Mail (DKIM) security related to insecure key management practices, highlighting the need for stronger email security measures and collaboration between organizations and email service providers.
Fast Facts
- Recent research has identified critical vulnerabilities in DomainKeys Identified Mail (DKIM) security, particularly related to the use of insecure RSA keys and inadequate key management practices.
- The study utilized automated security auditing tools and advanced factorization techniques to evaluate DKIM implementations and assess the susceptibility of RSA keys to attacks.
- Key findings revealed a high prevalence of short DKIM keys and outdated key management practices, highlighting the need for stronger configurations and public awareness campaigns.
- The research emphasizes the importance of collaboration between cybersecurity researchers and email service providers to develop enhanced security protocols for email communications.
- Future directions include investigating stronger DKIM key implementations and creating automated tools for organizations to audit their email security configurations.
In an era where digital communication underpins both personal and professional interactions, the security of email systems has never been more crucial. As cyber threats evolve, the mechanisms designed to protect our inboxes must also adapt. One such mechanism is DomainKeys Identified Mail (DKIM), which serves as a safeguard by allowing senders to sign their emails cryptographically. Yet, recent findings indicate that many organizations are operating with insecure DKIM keys, raising alarm bells across the cybersecurity landscape. This article delves into the critical implications of these vulnerabilities, the methodologies employed in their investigation, and what the future holds for DKIM security.
The foundation of this research lies in understanding the limitations of current key management practices. Insecure DKIM keys can lead to unauthorized access and data breaches, rendering previously trusted communications vulnerable. The implication is profound: organizations relying on weak key management may inadvertently expose themselves to sophisticated cyberattacks. Automated security auditing tools have surfaced as a promising solution to this issue, enabling organizations to regularly assess their email security configurations. Such tools not only streamline audits but also offer insights into potential weaknesses that could be exploited.
Among the interesting methodologies explored was the construction of RSA private keys and testing DKIM signatures. Here, researchers employed Python and PyCryptodome to decode RSA public keys and analyze their robustness against various attacks, including factorization of the RSA modulus—a process that remains a cornerstone of cryptographic vulnerability assessments. By utilizing cutting-edge techniques like CADO-NFS (Number Field Sieve), researchers were able to efficiently crack weaker DKIM signatures, shedding light on how even subtle oversights in key length can lead to catastrophic failures in email integrity.
The study also investigated the state of cloud computing environments, specifically looking at platforms like Hetzner. The intersection of cloud services and email security adds another layer of complexity, as organizations increasingly migrate sensitive communications to cloud-based infrastructures without fully understanding the security ramifications. This shift necessitates urgent public awareness campaigns aimed at educating businesses about the importance of robust email authentication methods, particularly when deploying cloud solutions.
Key findings from this research highlight not only existing vulnerabilities but also avenues for improvement. Collaboration with email service providers emerged as a vital strategy for enhancing DKIM security across the board. By working together, organizations can foster a comprehensive approach to secure key management practices, ensuring that all components of email infrastructure are fortified against emerging threats.
As we look ahead, it’s clear that there are several future directions worth exploring within DKIM security frameworks. The rise of automated tools will likely play a pivotal role in shaping how organizations manage their keys and audit their systems. Furthermore, as public awareness grows, we may see a push for industry-wide standards that mandate stronger key lengths and robust encryption methods—transforming how email authentication is perceived across sectors.
In conclusion, while the research underscores significant vulnerabilities associated with short DKIM keys and insecure practices, it also sheds light on proactive measures that can be taken to fortify defenses. The evolving landscape of cybersecurity demands vigilance and innovation; thus, stakeholders must remain committed to enhancing email security protocols for a safer digital communication environment moving forward. As cyber threats continue to morph, so too must our strategies for safeguarding one of our most fundamental communication tools—email.