
Defending Against Advanced Cyber Threats
/ 8 min read
In the ever-evolving landscape of cyber threats, understanding and anticipating adversarial tactics is crucial. This comprehensive guide explores Time-Based Security (TBS), the Intrusion Kill Chain, and the MITRE ATT&CK framework, demonstrating how integrating these models can fortify your organization’s defenses against sophisticated cyber adversaries.
Introduction
As cyber threats become more advanced, organizations must adopt comprehensive strategies to defend against sophisticated adversaries. Traditional security measures are no longer sufficient; instead, a multifaceted approach that combines various models and frameworks is necessary.
This blog post delves deep into:
- Time-Based Security (TBS): A quantitative method focusing on the timing aspects of protection, detection, and reaction.
- Intrusion Kill Chain: A model outlining the stages of a cyberattack, providing opportunities to disrupt the attacker’s progression.
- MITRE ATT&CK Framework: A detailed matrix of adversary tactics and techniques used to enhance detection and response capabilities.
By integrating these models, organizations can enhance their Security Operations Centers (SOCs) to block, detect, and react to threats more effectively.
Understanding Time-Based Security (TBS)
“Time is the enemy of security. The longer it takes to detect and respond to a breach, the greater the potential damage.” — Winn Schwartau, Time-Based Security
The TBS Equation
Time-Based Security (TBS), introduced by Winn Schwartau in his book Time Based Security: Adding Measurement, Detection, and Reaction Time to Cybersecurity, emphasizes the importance of timing in cybersecurity defenses.
The core components of TBS are:
- Protection Time (P): The duration your security measures can withstand an attack before failure.
- Detection Time (D): The time it takes to detect that an attack is occurring or has occurred.
- Reaction Time (R): The time required to respond and mitigate the attack after detection.
The fundamental TBS equation:
If P>(D+R), then the system is secure
This means that if your protection mechanisms can hold off an attack longer than it takes to detect and respond, your system remains secure.
Table 1: TBS Components Explained
| Component | Definition | Goal |
|---|---|---|
| P (Protection Time) | Duration defenses can withstand an attack | Maximize (Longer P) |
| D (Detection Time) | Time taken to identify a breach | Minimize (Shorter D) |
| R (Reaction Time) | Time to respond and mitigate after detection | Minimize (Shorter R) |
Applying TBS in Cybersecurity
TBS provides a quantitative approach to security budgeting and risk management by:
- Measuring Effectiveness: Quantifying how long defenses can hold and how quickly the organization can detect and respond.
- Supporting Decision-Making: Allocating resources effectively by understanding where to invest in protection, detection, or reaction capabilities.
- Reducing Exposure Time: Minimizing the window during which systems are vulnerable to attacks.
By addressing these questions, organizations can create strategies that reduce the overall risk and potential impact of cyberattacks.
The Intrusion Kill Chain Model
“The kill chain framework provides a way to understand the sequence of events that lead to a successful intrusion, allowing defenders to anticipate and disrupt attacks.” — Lockheed Martin
Stages of the Kill Chain
Developed by Lockheed Martin, the Intrusion Kill Chain is a model that outlines the steps adversaries follow to achieve their objectives. The term “kill chain” originates from military strategies aimed at identifying and disrupting enemy actions.
The seven stages of the Cyber Kill Chain are:
- Reconnaissance: Adversaries gather information about the target to identify vulnerabilities.
- Weaponization: Crafting malicious payloads tailored to exploit identified vulnerabilities.
- Delivery: Transmitting the weaponized payload to the target via email, USB drives, or other methods.
- Exploitation: Executing the malicious code on the target system.
- Installation: Installing malware to establish a persistent presence.
- Command and Control (C2): Establishing a communication channel to remotely control the compromised system.
- Actions on Objectives: Performing the intended actions, such as data exfiltration, destruction, or further network compromise.
Figure 1: The Intrusion Kill Chain Diagram
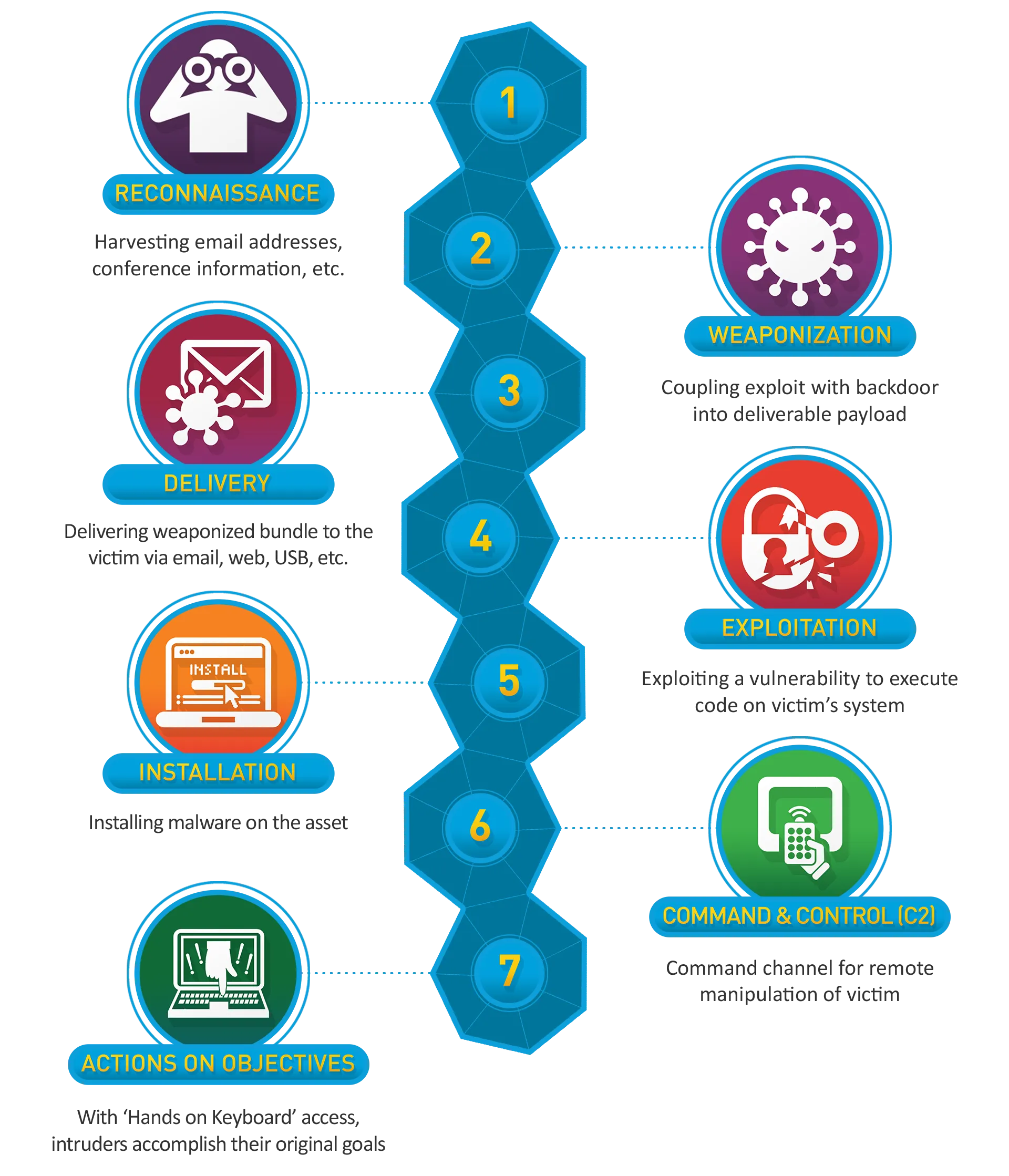
Breaking the Chain
The kill chain model emphasizes that interrupting any stage can prevent the attacker from achieving their objectives. By understanding each phase, defenders can implement specific controls to disrupt the attack progression.
Defensive Measures at Each Stage:
- Reconnaissance: Monitor for suspicious scanning activities; implement honeypots.
- Weaponization: Use threat intelligence to anticipate attack tools.
- Delivery: Implement email filtering, web proxies, and removable media controls.
- Exploitation: Patch vulnerabilities; employ intrusion prevention systems.
- Installation: Use application whitelisting; monitor for abnormal file changes.
- Command and Control: Detect anomalous outbound traffic; block known C2 domains.
- Actions on Objectives: Monitor for unauthorized data access; implement data loss prevention.
MITRE ATT&CK Framework
“MITRE ATT&CK provides a comprehensive matrix of adversary behaviors, enabling organizations to enhance their detection and response capabilities.” — MITRE
Tactics, Techniques, and Procedures (TTPs)
The MITRE ATT&CK framework is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. It categorizes adversary behaviors into:
- Tactics: The adversary’s technical goals during an attack (the “why”).
- Techniques: Specific methods used to achieve those goals (the “how”).
- Procedures: The specific implementations of techniques (the detailed “how”).
Table 2: Sample Tactics and Techniques
| Tactic | Techniques |
|---|---|
| Initial Access | Phishing, Drive-by Compromise, Supply Chain |
| Execution | Command-Line Interface, Scripting |
| Persistence | Registry Run Keys, Scheduled Tasks |
| Privilege Escalation | Exploitation for Privilege Escalation, Sudo Caching |
| Defense Evasion | Obfuscated Files, Disable Security Tools |
Comparison with the Kill Chain
While both models aim to understand and disrupt cyberattacks, they differ in scope and granularity.
Table 3: Kill Chain vs. MITRE ATT&CK
| Aspect | Intrusion Kill Chain | MITRE ATT&CK |
|---|---|---|
| Focus | High-level stages of an attack | Detailed adversary behaviors |
| Granularity | Broad phases | Specific tactics and techniques |
| Usage | Strategic planning | Tactical detection and response |
| Framework Type | Linear progression | Matrix of behaviors |
Key Differences:
- Detail Level: MITRE ATT&CK provides more detailed insight into specific adversary behaviors.
- Flexibility: ATT&CK can be applied at various points in the attack lifecycle, not just sequentially.
- Detection and Response: ATT&CK is more directly applicable to enhancing detection and response capabilities.
Integrating TBS, Kill Chain, and MITRE ATT&CK
Combining these models allows organizations to develop a robust defense strategy that anticipates, detects, and responds to cyber threats effectively.
Case Study: A Unified Defense Strategy
Scenario: An advanced persistent threat (APT) group targets a financial institution to exfiltrate sensitive customer data.
Step 1: Modeling Attacker Behavior with MITRE ATT&CK
- Initial Access (Tactic): Phishing emails with malicious attachments (Technique: Spearphishing Attachment).
- Execution: Malware executes upon opening the attachment (Technique: User Execution).
- Persistence: Malware installs a backdoor (Technique: Boot or Logon Autostart Execution).
- Command and Control: Establishes encrypted communication with C2 servers (Technique: Encrypted Channel).
- Exfiltration: Compresses and exfiltrates data (Technique: Exfiltration Over C2 Channel).
Step 2: Mapping to the Kill Chain
- Reconnaissance: Gathering employee emails and crafting targeted phishing messages.
- Weaponization: Creating malware-laden attachments.
- Delivery: Sending phishing emails to employees.
- Exploitation: Employee opens the attachment, executing the malware.
- Installation: Backdoor installed for persistent access.
- Command and Control: Remote control established.
- Actions on Objectives: Data exfiltration begins.
Step 3: Applying Time-Based Security (TBS)
- Protection Time (P): Email filters and antivirus software delay or prevent malware execution.
- Detection Time (D): Security monitoring detects unusual outbound traffic within 2 hours.
- Reaction Time (R): Incident response team contains the breach within 1 hour of detection.
Outcome: By integrating these models, the SOC can:
- Block the attack at the delivery stage using email filters.
- Detect the breach quickly through monitoring aligned with ATT&CK techniques.
- React swiftly by containing and eradicating the threat.
Benefits:
- Early Warning Indicators: Multiple detection points before the attacker reaches their objective.
- Prioritized Responses: High-fidelity detections receive immediate attention.
- Reduced Exposure Time: Minimizes potential damage and data loss.
The Incident Response Hierarchy of Needs
“Effective incident response requires a foundation of capabilities, each building upon the other to support a resilient security posture.”
Building a Strong Foundation
The Incident Response Hierarchy of Needs outlines the essential capabilities organizations must develop for effective incident response:
- Preparation: Policies, procedures, and training.
- Detection and Analysis: Monitoring, threat intelligence, and analytics.
- Containment, Eradication, and Recovery: Actions to limit damage and restore operations.
- Post-Incident Activity: Lessons learned and process improvements.
Figure 2: Incident Response Hierarchy Pyramid
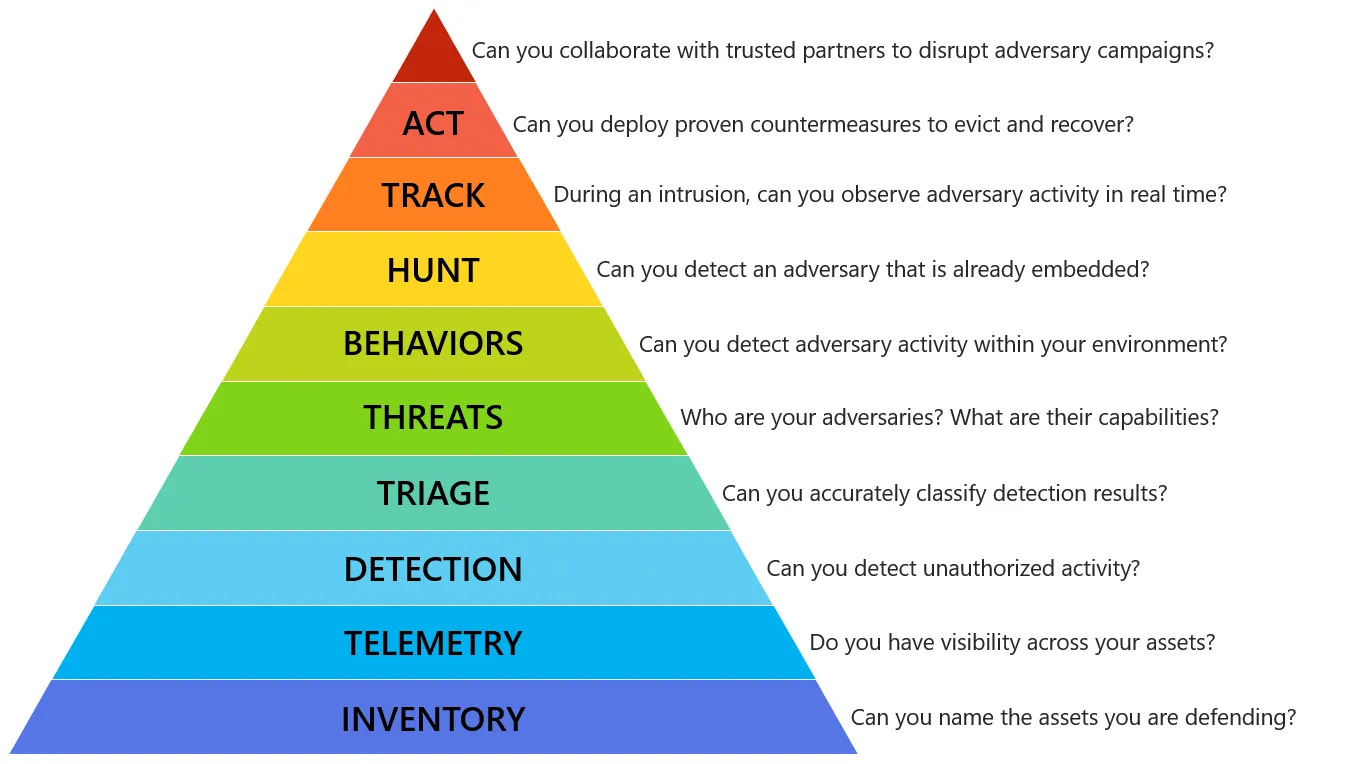
Key Components:
- Visibility: Understanding what’s happening in your environment.
- Detection: Identifying malicious activities promptly.
- Analysis: Investigating incidents to determine scope and impact.
- Action: Implementing measures to contain and eliminate threats.
By addressing each layer, organizations ensure that their incident response capabilities are robust and effective.
Lessons from Physical Security
“Time-based security principles are not new; they’ve been applied in physical security for decades to protect assets from theft and damage.”
Safe Ratings Explained
In the physical world, safes are rated based on their ability to resist attacks from burglars and protect against fire. The time a safe can withstand an attack is crucial in determining its effectiveness.
Types of Safe Ratings:
- Residential Security Container (RSC): Resists entry for up to 5 minutes using simple tools.
- Burglar Safes: Rated by the time they can resist attacks using various tools.
- B Rate: Basic protection, 1/2” steel door.
- C Rate: More protection, 1” steel door.
- TL-15: Resists attack for 15 minutes with common tools.
- TL-30: Resists attack for 30 minutes.
Table 4: Safe Ratings and Protection Time
| Rating | Protection Time | Attack Tools Resisted |
|---|---|---|
| RSC | 5 minutes | Simple hand tools |
| B Rate | N/A | Limited protection |
| C Rate | N/A | Enhanced protection |
| TL-15 | 15 minutes | Common mechanical and electrical tools |
| TL-30 | 30 minutes | Advanced tools, including cutting torches |
Conclusion
In an era where cyber threats are increasingly sophisticated, organizations must adopt a comprehensive defense strategy. By integrating Time-Based Security (TBS), the Intrusion Kill Chain, and the MITRE ATT&CK framework, security teams can:
- Anticipate Adversary Actions: Model attacker behaviors to stay one step ahead.
- Enhance Detection Capabilities: Identify threats early using detailed TTPs.
- Optimize Response Times: Reduce detection and reaction times to minimize exposure.
- Support Tactical Decision-Making: Provide context for security operations to make informed decisions.
Final Thoughts:
Combining these models enables a proactive defense posture. Security Operations Centers can effectively block, detect, and react to threats as early as possible, reducing the overall risk and impact of cyberattacks. By investing in these integrated strategies, organizations strengthen their resilience against advanced adversaries.
Protecting your organization requires not just tools, but a deep understanding of adversary behaviors and timely responses. By integrating these models, you’re not just reacting to threats—you’re anticipating and neutralizing them before they can cause harm.


